
Azure 900 Certification 2024 – AZ-900 Knowledge Point Summary – Online Practice, Certificate

Combined with the recent simulation questions, review and record some knowledge and concepts that are easy to test. Pay attention to the words marked in red. These simple words may be the key points that can best summarize this concept. When I review, I have highlighted these points in red and will use different case forms in the question stem. Come to inspect, but the keywords for these inspections can still be found! It is recommended to print it out and study it if possible. I summarized it bit by bit from the official document. The test points are very comprehensive. So far, the journey of AZ-900 has been completed. At the end of the article, a screenshot of the certificate and a personal learning route are attached. If you are interested, you can read it. I hope everyone can pass the AZ-900 as soon as possible!
Table of contents:
- Analysis Summary: Exploring Cloud Concepts
- Analysis Summary: Exploring Core Services
- Analysis Summary: Azure Security, Privacy, Compliance, and Trust (revolving around security)
- Analysis Summary: Review, Pricing, Service Level Agreements and Lifecycle
- AZ-900 online practice
- Certificate summary
Part 1, Exploring Cloud Concepts
1. What is cloud service?
- High availability. The ability to keep a service uptime for an extended period of time with minimal downtime, depending on the service in question.
- Scalability. The ability to increase or decrease resources for any given workload. You can add additional resources to serve your workload (known as scaling out), or add additional capabilities to manage increased demand on existing resources (known as scaling out). Scalability doesn’t have to be automatic.
- Elasticity. The ability to automatically or dynamically increase or decrease resources as needed. Elastic resources can meet current demand, and resources can be automatically added or removed as needed (and from the most advantageous geographical location) to meet future demand. The difference between scalability and elasticity is that elasticity is done automatically.
- Agility. Ability to react quickly. Cloud services can quickly allocate and reallocate resources. They are provided on-demand through self-service, so large amounts of computing resources can be provisioned in minutes. No manual intervention is required in provisioning or de-provisioning services.
- Fault tolerance. The ability to maintain normal operation even when a component (or service) is not functioning properly. Typically, redundancy is built into the cloud service architecture, so if one component fails, a backup component will be used instead. The service is said to be fault-tolerant.
- Disaster recovery. The ability to recover from an event that shuts down cloud services. Cloud service disaster recovery can be performed very quickly, with automation and services readily available.
- Global coverage. The ability to reach a global audience. Cloud services can operate in various regions around the world that you and your customers can access, even if you don’t have any infrastructure in the region.
- Customer delay function. If customers feel slow when using a particular cloud service, then they are said to be experiencing some latency. Even though modern fiber optics are fast, it still takes time for the service to respond to the customer’s actions if the service is not local to the customer. Cloud services can deploy resources in data centers around the world to address any customer latency issues. (Deploy resources based on customer location)
- Predictable cost considerations. The ability for users to predict the costs that specific cloud services will incur. Costs for individual services are provided, and tools are provided to allow you to predict the costs that will be incurred by the services. You can also perform analysis based on planned growth.
- Technical skill requirements and considerations. Cloud services can provide and manage hardware and software for workloads. Using cloud services to ramp up workloads and run them requires fewer technical resources than having IT teams build and maintain the physical infrastructure used to handle the same workloads. Users can be experts in the applications they want to run without requiring the skills to build and maintain the underlying hardware and software infrastructure.
- Increase productivity. On-site data centers often require extensive hardware setup (also known as racks and stacks), software patching, and other time-consuming IT management tasks. Cloud computing eliminates the need for many of these tasks. This allows IT teams to spend time focusing on achieving more important business goals.
- Safety. Cloud providers offer a broad range of policies, technologies, controls, and expert technical skills that can provide better security than most organizations can achieve. The result is enhanced security, which helps protect data, applications, and infrastructure from potential threats.
Capital expenditure CapEx and operating expenditure OpEx: Click here to view the official detailed explanation
- Capital Expenditure (CapEx): This refers to the upfront expenditure on physical infrastructure, which is then deducted over time. The value of the upfront cost of CapEx decreases over time. Capital expenditures are when you spend money on physical infrastructure upfront and then deduct that expenditure from your tax bill over time. My understanding is that it is the upfront cost of hardware.
- Operating Expenses (OpEx): This is money spent on services or products for which you are now paying. You can deduct this expense in the same year you spend it. There are no upfront fees because you pay when you use the service or product. Operating expenses are expenses incurred on an ongoing basis while you use a given service or feature. My understanding is that it is the operating expenses between making money and making preparations for your product.
2. Differentiate cloud model types
In summary, it is public cloud, private cloud, hybrid cloud
Public cloud:
Public clouds are owned by cloud service providers (also known as hosting providers). It provides resources and services to multiple organizations and users who connect to cloud services through secure network connections, usually over the Internet.
Public cloud features:
- Ownership – Ownership refers to the resources used by the organization or end users. Examples include storage and processing capabilities. Resources do not belong to the organization that uses them but are owned and operated by a third party (such as a cloud service provider).
- Multiple End Users – Public cloud models can make their resources available to multiple organizations.
- Public Access – Public access allows the public to access required cloud services.
- Availability – Public cloud is the most common cloud-type deployment model.
- Connectivity – Users and organizations often use web browsers to connect to public clouds over the Internet.
- Skills – Public clouds do not require in-depth technical knowledge to set up and use their resources.
Private Cloud:
A private cloud is owned and operated by the organization that uses the resources in the cloud. They create cloud environments in their own data centers and provide self-service access to computing resources to users within the organization. The organization remains the owner and is fully responsible for the operation of the services it provides.

Private cloud features:
- Ownership. The owner and user of a cloud service are the same.
- Hardware. The owner is fully responsible for the purchase, maintenance, and management of cloud hardware.
- User. A private cloud operates within only one organization and uses only cloud computing resources for a single business or organization. (This aspect involves privacy security)
- Connectivity. Connections to private clouds are typically via highly secure private networks.
- Public access. Access is not provided to the public.
- Skill. Requires in-depth technical knowledge to set up, manage, and maintain.
Starting point for the test questions:
The use case scenario for the private cloud is when an organization is unable to put data into the public cloud due to legal reasons. For example, they may have medical data that cannot be made publicly available.
Another scenario might be that government policy requires certain data to be kept domestic or private.
Private clouds can also provide cloud capabilities to external customers or specific internal departments (such as accounting or human resources)
Hybrid cloud:
Hybrid cloud combines public and private clouds, allowing you to run applications where they make the most sense. (Hybrid cloud is the best choice at any time)
Starting point for the test questions:
An example of a hybrid cloud use scenario is hosting a website in a public cloud and linking it to a highly secure database hosted in a private cloud.
Hybrid cloud scenarios are useful when an organization has something that may not be put into the public cloud for legal reasons. For example, you may have medical data that cannot be made publicly available;
Another example is one or more applications that cannot run on older hardware. In this case, you can keep the legacy system running locally in a private cloud and connect it to the public cloud for licensing or storage. I have encountered these two cases in the question
Compare cloud models: View official documentation
Compare based on your needs, considering the pros and cons of public cloud, private cloud, and hybrid cloud
Public Cloud: The most common deployment model, there is no hardware to manage and everything is on the cloud provider.
Pros and cons of public cloud: Advantages, no CapEx capital expenditure, can be expanded without buying new servers, agile provisioning (no need to buy and set up infrastructure), runs using OpEx consumption model, does not need to worry about the repair and maintenance of hardware, does not require deep technical knowledge Technical skills can rely on the skills and knowledge of the cloud provider to ensure job security and high availability; Disadvantages, lack of security, compliance (inability to meet government, legal requirements), no hardware management rights.
Private Cloud: Create a cloud environment in your own data center and purchase and maintain hardware and software services yourself
Advantages and Disadvantages of Private Cloud: Advantages, are full control over resources, security, compliance, and specific solutions (coexistence of new and old program versions); Disadvantages, because of full control over resources, there must be CapEx upfront capital expenditure, no agility ( To purchase and set up the infrastructure), regular care and maintenance, requires specialist IT skills and knowledge
Hybrid Cloud: You know it as soon as you hear it, a mix of public and private clouds
Advantages and Disadvantages of Hybrid Cloud: Advantages, flexibility, reasonable cost, control, security, compliance, and specific solutions; Disadvantages, before utilizing private cloud, you still need upfront capital expenditure and cost (maintenance and purchase of private cloud and public cloud at the same time, to More expensive than a single deployment model), skills, easy to manage
3. Explore cloud service types
This chapter mainly introduces the three types of cloud computing services: Iaas, Paas, and Saas. Personally, I prefer this order to remember. The underlying infrastructure as a service of IAAS is similar to the virtual machine VM operating system storage. The top is the development layer Paas platform. As-a-service SQL database, and above that is software using Saas software-as-a-service such as office365 forms, etc.!
a. Iaas service type
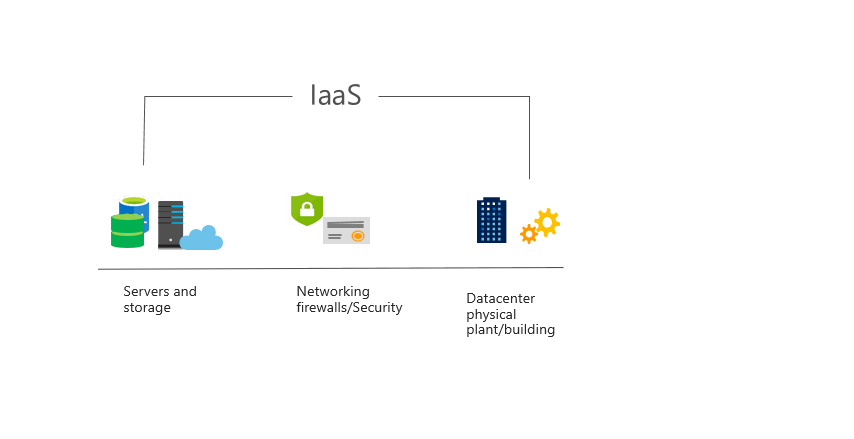
Iaas features: no upfront costs, you only need to pay for what you consume; user ownership, users are responsible for purchasing, installing, configuring, and managing their own software operating systems, middleware, and applications; cloud provider ownership, the cloud provider is responsible for ensuring Users can use infrastructure (such as virtual machines, network and storage)
Iaas usage scenarios: Migration, a simple understanding is a path to migrate existing programs to the cloud; testing and development, you can quickly test and develop the environment, if the deployment is bad, there is no problem to delete it and start again; website hosting, using Iaas is cheaper than traditional servers; Storage, backup and recovery, avoiding the capital expenditure and complexity of storage management, simplifying the process of backing up and restoring systems
b. Paas service type
The platform is a service, that provides an environment for building, testing, and deploying software programs; PaaS is designed to be customized for developers, and there is no need to worry about the underlying infrastructure, install the operating system, or update the system yourself.
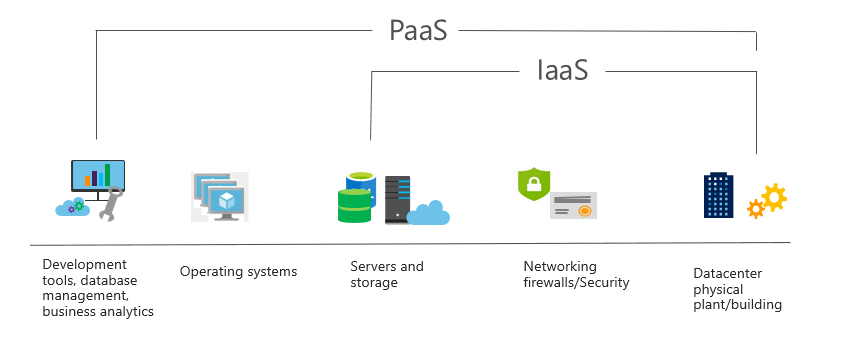
Paas features: Like Iaas, there is no upfront cost, and consumption is deducted on demand; also like Iaas, it has user ownership and cloud provider ownership;
Paas usage scenarios: Development framework, developers can use the framework provided by Paas as a basis to develop customized cloud-based applications, including cloud features such as scalability, high availability, and multi-tenant capabilities, thereby reducing the coding that developers must perform Volume; provides intelligent analytics tools that enable organizations to analyze and mine their data. They can uncover insights and patterns and predict outcomes to improve business decisions such as forecasting, product design, and return on investment.
c. Sass service type
Saas is the top-level cloud computing service type. Just like the software you use on your computer, you don’t need to care about the computer system or the software development language. You only need to focus on how the software you want to use can help you. For example, Outlook email, Microsoft 365; and Saas is usually licensed through monthly or annual subscriptions; here I encountered a knowledge point, what is the charging model of Saas?
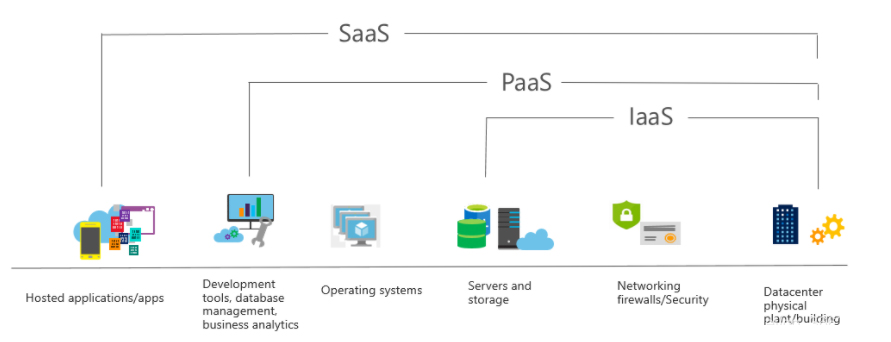
Saas characteristics: The cost of Saas is different from that of Iaas and Paas. Saas is charged separately. Because it is a property product, the fee is usually monthly or annual, while Iaas and Paas are billed on demand;
Saas usage scenarios: Examples of Microsoft SaaS services include Microsoft 365, Skype, and Microsoft Dynamics CRM Online.
Compare cloud service types:
Iaas advantages and disadvantages:
Advantages: 1. No capital expenditure, no upfront costs. 2. Agility to quickly access and configure used applications. 3. Consumption model, OpEx is billed on demand. 4. High availability. The skills and expertise of the cloud provider will ensure that the workload is secure and highly available. 5. Flexible, Iaas is the most flexible cloud service that can control the configuration and management of application hardware
Disadvantages: Management and sharing of responsibilities means that you have to manage the operating status of the virtual machines to see if the load is too high and whether the running software is legal and compliant; users themselves manage and maintain the services they are responsible for, and the cloud provider manages and maintains the cloud infrastructure.
Paas advantages and disadvantages:
Advantages: 1. No upfront fees, charges are based on demand. 2. Agility, there is no need to configure the server separately and install a Linux or Windows server system. 3. No particularly high skills are required. 4. The advantages of the cloud are high availability, disaster recovery, etc.
Disadvantages: Platform limitations, you need to consider which PaaS platform is most suitable for the workload. I don’t quite understand this sentence.
SaaS advantages and disadvantages:
To put it bluntly, Saas is a developed software for you to use. It is usually charged on a monthly or annual basis. There is not much to say.
Advantages: 1. No upfront costs. 2. Agility and quick access to software. 3. Pricing as you use it, charged monthly or annually. 4. High flexibility, you can access the same program data anywhere, such as on PC and mobile terminals
Disadvantages: software limitations, affecting the way users work IaaS, PaaS, and SaaS each contain different levels of hosting services. You can easily combine these types of infrastructure. You can use Microsoft 365 on your company’s computers (SaaS), host VMs in Azure (IaaS), and store data using Azure SQL Database (PaaS). With the flexibility of the cloud, you can use any combination that gives you maximum results. Pay attention to these places marked in red, they are standard test points!
Part 2, Exploring Core Services
1. Azure core architecture components
1. Region, to understand it is that when deploying resources, you have to look at where you are and which region of the cloud you want to choose! (such as the Americas, Europe, Asia Pacific, East Central, and Africa)
2.Regional pairs. To simply understand, regional pairs are created to deal with disasters.
Area Pair Notes:
Physical isolation. Where possible, Azure wants to maintain a minimum distance of 300 miles between data centers in regional pairs, although this may not be feasible or possible in all regions. The separation of physical data centers reduces the likelihood of a natural disaster, civil unrest, power outage, or physical network outage affecting both areas simultaneously.
Replication provided by the platform. Some services (for example, geo-redundant storage) provide automatic replication to paired regions.
Zone recovery sequence. In the event of a widespread outage, recovery is prioritized for one area in each pair. Applications deployed across paired regions ensure that one region is restored first.
Sequential updates. Scheduled Azure system updates are deployed to paired regions sequentially (rather than simultaneously) to minimize downtime, the impact of errors, and logical failures in the unlikely event of a bad update.
3. Availability sets are a method of keeping applications online when a major maintenance event or hardware failure occurs.
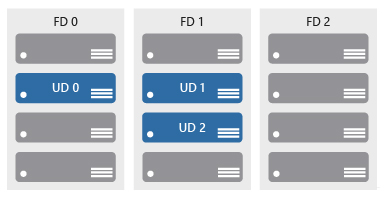
Availability sets consist of update domains (UP) and fault domains (FD)
Update domain. When a maintenance event occurs (for example, a performance update or a critical security patch applied to a host), updates are ordered by the update domain. Sequencing updates using update domains ensures that the entire data center is unavailable during platform updates and patching processes. Update domains are logical parts of the data center and they are implemented through software and logic.
Fault domain. Fault domains provide physical isolation of workloads across different hardware in the data center. This includes power, cooling, and networking hardware to support the physical servers located in the server racks. If the hardware supporting a server rack is unavailable, only that server rack is affected by the outage.
4. Availability Zones are used to ensure that services and data are redundant to protect information in the event of a failure. When you host infrastructure, you need to create duplicate hardware environments and make your applications highly available with the help of Availability Zones.
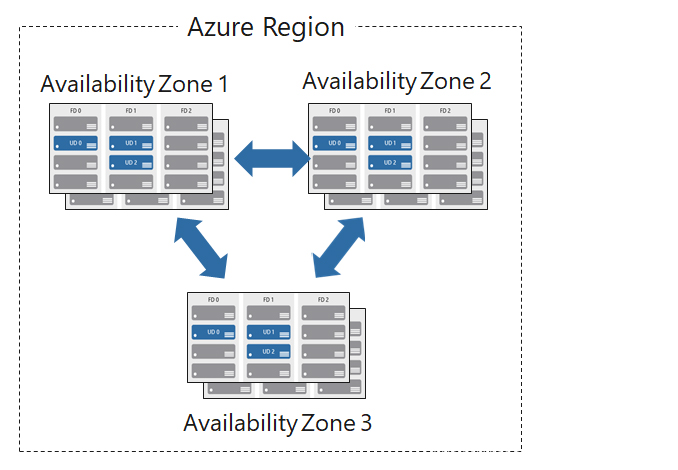
Availability zone features:
- Physical isolation, each Availability Zone is an isolation boundary containing one or more data centers equipped with independent power, cooling, and networking capabilities.
- If one Availability Zone goes down, the other one continues to work.
- Availability Zones are typically connected to each other via a very fast private fiber network.
- Availability Zones allow customers to run mission-critical applications with high availability and low-latency replication.
- Availability Zones are a service within Azure, and to ensure resiliency there must be at least three separate regions across all enabled zones.
Regions that support Availability Zones include Central America, Northern Europe, Southeast Asia, etc.
Using Availability Zones in your application:
You can use availability zones to run mission-critical applications and build high availability into your application architecture by colocating compute, storage, network, and data resources in one zone and replicating them in other zones. Keep in mind that there may be costs for replicating services and transferring data between regions. (This sentence has appeared in the test site. There is no charge for creating an availability zone, but there will be costs for copying services and transmitting data)
Availability Zones are mainly used for VMs, managed disks, load balancers and SQL databases. Azure services that support Availability Zones are divided into two categories:
- Zone Services – you pin resources to a specific zone (e.g. virtual machines, managed disks, IP addresses)
- Zone-redundant services – The platform automatically replicates across regions (e.g., zone-redundant storage, SQL databases).
5. Resource group, a resource group is a logical grouping of managed resources, placing a series of resources in the same resource group. Note that when you delete a resource group, all resources in the resource group will be deleted! Grouping is a means of logically grouping management according to different functions or departments according to your own grouping preferences. Easy to manage
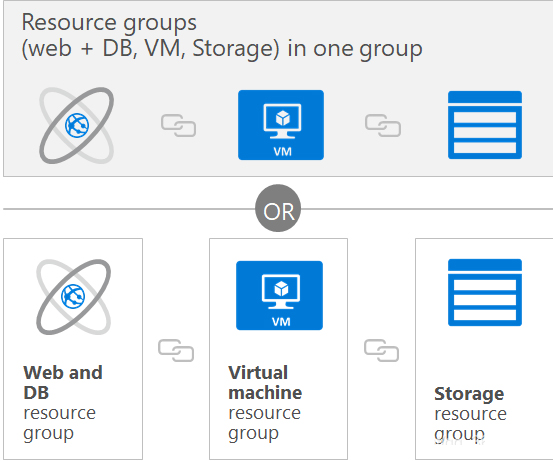
Notes on resource groups:
- Each resource must exist in a resource group and can exist in only one resource group.
- Resource groups can contain resources that reside in different regions.
- You decide how to assign resources to resource groups based on what makes the most sense for your organization.
- You can add or remove resources from a resource group at any time.
- You can move resources from one resource group to another.
- An application’s resources do not have to exist in the same resource group. However, it is recommended that you keep them in the same resource group for easier management.
- Unified life cycle management, deleting a resource group will delete all resources in it
Authorization:
Role-based access control (RBAC) simplifies management by applying RBAC permissions to resource groups and restricts access to only allow required content to be displayed.
How to create a resource group:
1. Azure portal 2. Azure PowerShell command line 3. Azure CLI 4. Template 5. Azure SDK (.net, Java) developer call
Organize usage in billing reports:
Finally, placing resources in the same resource group is a way to group them for use in billing reports. If you are trying to understand how costs are allocated in your Azure environment, grouping costs by resource group is a way to filter and sort the data to better understand how costs are allocated.
Azure Resource Manager: Simply understand, it is the way to manage Azure resources (create, configure, manage, delete resource groups), you can use different automation and scripting tools (such as Microsoft Azure PowerShell, Azure command line interface ( Azure CLI), Azure portal, REST API and client SDK) to automate the deployment and configuration of resources
2. Define Azure core services and products
Define Azure Compute: Provides on-demand computing services for cloud-based applications. It provides computing resources such as disks, processors, memory, network, and operating system. Resources are provided on demand. This should be clear and you pay for the resources you use. The next part is to discuss separately the main centralized computing resources above!
VM virtual machine (Iaas service): It is a software simulation of a physical virtual machine, including virtual processor, memory, storage, and network resources. A VM hosts an operating system, and you can install and run software just like a physical computer. Virtual machine types include Linux, Windows Server, Microsoft SQL server, Oracle, IBM, and SAP.
Virtual Machine Scale Set: This can be used to deploy and manage a group of identical VMs. Virtual machine scale sets are designed to support true automatic scaling when all virtual machines are configured identically. There is no need to pre-configure virtual machines; this makes it easy to build large-scale services for large computing, big data, and containerized workloads. Therefore, as demand increases, more virtual machine instances can be added, and as demand decreases, virtual machine instances can be removed. The process can be manual, automated, or a combination of both.
App services: Used to quickly build, deploy, and scale enterprise-class web, mobile, and API applications running on any platform. Paas service
Functions: Ideal when you only want to focus on the code that runs the service, not the underlying platform or infrastructure. They are typically used when you need to perform work in response to a time, usually, REST, request, timer, or message from another service in Azure, and the work can be completed in a few seconds or less.
Container Service Container: A container is a virtualized environment and there are two ways to manage Docker and Microsoft-based containers in Azure. 1. Azure Container Instance provides the fastest and easiest way to run containers in Azure without having to manage any virtual machines or adopt any other services. It is a PaaS product that lets you upload a container and it will run for you. 2. Azure Kubernetes (K8S),
Azure Network Services: Network services in Azure allow you to connect cloud and on-premises infrastructure and services. When general resources are migrated to Azure, they generally need to perform the same network functions as local deployments. In specific cases, some degree of network isolation may be required.
Azure Virtual Network: Enables multiple types of Azure resources (such as VMs) to communicate securely with each other, the Internet, and local networks. The scope of a virtual network is limited to one zone. However, you can use virtual network peering to connect multiple virtual networks in different regions. With Azure Virtual Network, you can provide isolation, segmentation, communication with on-premises and cloud resources, routing and filtering of network traffic.
Azure Load Balancer: Can provide scale to your applications and create high availability for your services. LB (Load Balance) supports both inbound and outbound scenarios, provides low latency and high throughput, and scales to millions of flows for all Transmission Control Protocol (TCP) and User Datagram Protocol (UDP) applications. You can use LB for incoming Internet traffic, internal traffic between Azure services, port forwarding for specific traffic, or outbound connections to VMs in a virtual network. (The last bunch can be simply understood as four words, port forwarding)
Virtual Private Network (VPN): A VPN gateway is a specific type of virtual network gateway used to send encrypted communications between an Azure virtual network and an on-premises location over the public Internet
Azure Application Gateway: A web traffic load balancer that allows you to manage traffic for web applications. Users connect to your application through this connection, and using application gateway, traffic can be routed to the destination IP address and port based on the source IP address and port. You can also help protect your web applications with web application firewalls, redirects, keeping users on the same server, session affinity, and many other configuration options.
Content Delivery Network (CDN): A distributed network of servers that can deliver web content to users via email. It is a method of providing content to local users with minimal latency. The CDN can be hosted on Azure or any other location. You can cache content on physical nodes in strategic locations around the world and provide better performance to end users. Typical usage scenarios include web applications with multimedia content, product launch events in a region, or any event with high bandwidth needs in a region.
Define Azure data categories: In short, they are divided into three types: structured, semi-structured, and unstructured. When you store data, check the numbers separately, and then choose the corresponding storage plan. Screenshot below
Azure Storage: A service for storing files, messages, tables, and other types of information. You can use Azure Storage on its own (for example, as a file share), but developers also often use it as a work data store. Websites, mobile apps, desktop apps, and many other types of custom solutions can use this type of store. Some of the most common storage service types in Azure are disk, file, object, queue, and table.
Disk storage: Generally, disk storage is prepared for virtual machines. Disk storage allows for persistent storage and access to data. Disks are available managed by Azure or unmanaged and therefore managed and configured by the user. Typical scenarios for using disk storage are if you want to promote and move applications that read and write data to persistent disks, or if you want to store data that does not need to be accessed from outside the virtual machine attached to the disk.
Container (Blob): Cloud object storage solution. Blob storage is optimized to store large amounts of unstructured data, such as text or binary data. Pictures, documents, files, videos or audios.
Files: Azure Files allows you to set up a high-availability network file share that can be accessed using the standard Server Message Block (SMB) protocol. This means multiple VMs can share the same file with read and write access. You can also read the file using a REST interface or storage client library. One thing that differentiates Azure Files from files on a corporate file share is that you can access files from anywhere in the world using a URL pointing to the file and including a Shared Access Signature (SAS) token. You can generate SAS tokens; they allow specific access to private assets for a specific period of time.
Queue: Queue service is used to store and retrieve messages. The maximum queue message size is 64KB. A queue can contain millions of messages. Queues are typically used to store lists of messages to be processed asynchronously. For example, let’s say you want your customers to be able to upload images, and you want to create a thumbnail for each image. You can have your customers wait for you to create a thumbnail when they upload an image. Another option is to use a queue. After the client completes the upload, a message is written to the queue. Then let the Azure Function retrieve the message from the queue and create the thumbnail. Each part of this processing can be scaled individually, giving you more control when adjusting for use.
Tables: Used to store structured data, such as commonly used SQL databases, MYSQL, etc., which can accept authentication calls from within and outside the Azure cloud.
Azure Database Service: Complete PaaS service. Such as Cosmos database, SQL Server database!
Database Migration: Azure Database Migration Service refers to seamless migration from multiple database sources to the Azure data platform with minimal downtime!
3. Azure Solutions (mainly what you need to know)
My understanding is that this chapter mainly discusses the Internet of Things IOT and data analysis.
IoT: People have access to more information than ever before. It started with personal digital assistants (PDAs) and then evolved into smartphones. There are now smart watches, smart thermostats, and even smart refrigerators. Personal computers used to be the standard. The Internet now allows any online project to access valuable information. In Internet of Things (IoT) devices have the ability to collect and then relay information for data analysis. There are many services that assist and drive IoT end-to-end solutions on Azure. Two of the core Azure IoT service types are Azure IoT Central and Azure IoT Hub.
IoT Central: is a fully managed, global IoT Software-as-a-Service (SaaS) solution that makes it easy to connect, monitor and manage your IoT assets at scale. You don’t need a cloud expert to use IoT Central. As a result, you can bring connected products to market faster while maintaining focus on your customers. Network-friendly services
Azure IOT Hub: A managed service hosted in the cloud that acts as a central messaging hub for two-way communication between IoT applications and the devices they manage. Heart. There are too many professional terms, remember two words, monitoring!
Big data and analytics: Azure Synapse, Azure HDInsight, Azure data lake
Artificial intelligence: including image recognition, voice services, language conversion, brain recognition, knowledge resource integration, recommendation systems, and machine learning services
Serverless computing: mainly Azure functions, Azure logic Apps logic applications, Azure Event Grid event grid
Azure Features are ideal when you only focus on the code that runs the service and not the underlying platform or infrastructure. Azure Functions are typically used when you need to perform work in response to an event (usually via a REST request, a timer, or a message from another Azure service) and the work can be done quickly, in a few seconds or less. Additionally, Azure Functions are stateless; they behave as if they are restarted each time in response to an event. This is ideal for processing incoming data. And, if state is required, they can be connected to an Azure storage service.
Logic Apps is a cloud service that helps you automate and orchestrate tasks, business processes, and workflows when you need to integrate applications, data, systems, and services across your enterprise or organization. Logic Apps simplifies how you design and build scalable solutions for application integration, data integration, systems integration, enterprise application integration (EAI) and business-to-business (B2B) integration – whether in the cloud, on-premises or of the two). These include services such as Salesforce, SAP, Oracle DB and file sharing
Event Grid makes it easy to build applications using event-based architecture. This is a fully managed intelligent event routing service that uses a publish-subscribe model to unify event consumption. Event Grid has built-in support for services from Azure (you can use Event Grid to support your own non-Azure based events in near real-time using custom topics. You can use filters to route specific events to different endpoints, and Ensure events are delivered reliably.
Azure DevOps: Provides development collaboration tools including high-performance pipelines, free private Git repositories, configurable Kanban boards, and extensive cloud-based automated testing. DevOps Services was formerly known as Visual Studio Team Services (VSTS).
Azure Lab service: helps developers and testers quickly create environments in Azure while minimizing waste and controlling costs. Users can quickly configure Windows and Linux environments using reusable templates and artifacts to test their latest application releases. You can easily integrate your deployment pipeline with DevTest Labs to provide an on-demand environment. With DevTest Labs, you can scale load testing by configuring multiple test agents and creating pre-set environments for training and demonstrations. Lab Services was formerly known as DevOps Testing.
Azure App Service: Quickly and easily build web and mobile applications for any platform or device. Azure App Service lets you build and host web applications, mobile backends, and RESTful APIs using the programming language of your choice without having to manage infrastructure. It provides autoscaling and high availability, supports both Windows and Linux, and supports automated deployment from GitHub, Azure DevOps, or any Git repository.
4. Azure management tools
Azure management tools: You can use a variety of tools and platforms to configure and manage Azure. There are tools available for the command line, language-specific software development kits (SDKs), developer tools, migration tools, and many others. At the test site, you will be asked which option you can use to manage Azure resources.
- Azure Portal: It is a public website, the web side of Azure, which can be accessed using any web browser!
- Azure PowerShell: Azure PowerShell is a module added to Windows PowerShell or PowerShell Core that allows you to connect to your Azure subscription and manage resources. Azure PowerShell requires Windows PowerShell to run. PowerShell provides services such as shell windows and command parsing. Azure PowerShell will then add Azure-specific commands.
- Azure Command Line Interface (CLI): Azure CLI is a cross-platform command line program that can connect to Azure and execute management commands on Azure resources. Cross-platform means it can run on Windows, Linux or macOS.
- Azure Cloud Shell: Azure Cloud Shell is a browser-based scripting environment in your portal. It provides the flexibility to choose the shell experience that best suits the way you work. Linux users can choose the Bash experience, while Windows users can choose PowerShell.
- Azure Mobile App: The Microsoft Azure mobile app allows you to access, manage, and monitor all your Azure accounts and resources from your iOS or Android phone or tablet.
- Azure REST API: The Representational State Transfer (REST) API is a service endpoint that supports a set of HTTP operations (methods) that provide create, retrieve, update, or delete access to service resources. The REST API defines a set of functions that allow developers to perform requests and receive responses via HTTP protocols such as GET and POST.
Azure Advisor: A free service built into Azure that provides advice on high availability, security, performance, and cost. The Advisor analyzes your deployed services and looks for ways to improve your environment in these four areas. Test points
What can be done?
1. Get proactive, actionable and personalized best practice advice.
2. Improve the performance, security, and high availability of resources while identifying opportunities to reduce overall Azure costs.
3. Suggest actions and obtain suggestions.
Part 3, Azure Security, Privacy, Compliance and Trust (revolving around security)
1. Secure network connection
Azure Firewall: A firewall is a service based on granting server access to the source IP address of each request. You create firewall rules that specify IP address ranges. Only clients within these granted IP addresses will be allowed to access the server. Firewall rules also include specific network protocol and port information. NOTE: Firewall is a cloud-based managed network security service (Port Firewall); a fully stateful firewall-as-a-service built with high availability and unlimited cloud scalability.
Azure Distributed Denial of Service Protection DDos: Attacks attempt to overwhelm and exhaust an application’s resources, making the application slow or unresponsive to legitimate users. DDoS attacks can target any endpoint that is publicly accessible over the Internet. Therefore, any resource exposed to the Internet, such as a website, may be at risk from a DDoS attack. My personal understanding is that it seizes your server resources and prevents your program from executing normally.
Network Security Group Nsg: Allows you to filter network traffic between Azure virtual networks and Azure resources. NSG can contain multiple inbound and outbound security rules, allowing you to filter traffic to and from your resources by source and destination IP address, port, and protocol. To simply understand, it is the rules that restrict inbound and outbound traffic. Note: NSG can work in two places, 1 on the subnet and 2 on the network card.
Defense in Depth: A layered approach that provides multiple levels of protection mechanisms
Application Security Groups: Network security can be configured as a natural extension of the application structure, allowing virtual machines to be grouped and network security policies defined based on these groups. Application security groups help simplify how network traffic entering your organization is filtered and controlled and how network traffic is allowed to move. They enable you to isolate multiple workloads and provide a higher level of protection to your virtual network in a more manageable manner.
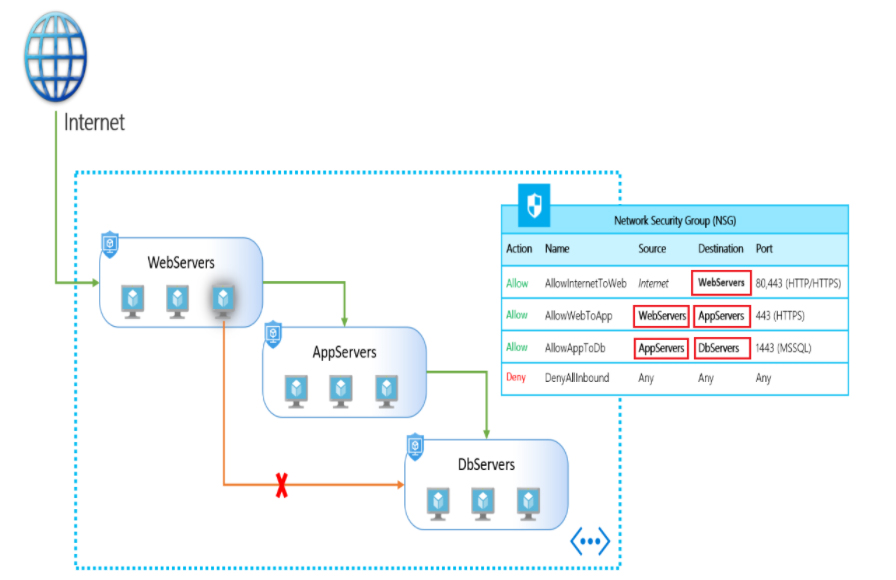
Azure Network Security Solutions
When considering security options, try to consider all elements;
Peripheral layer:
The network perimeter layer is used to protect your organization from network-based attacks against your resources. Identifying these attacks, raising alerts and neutralizing their impact is important to ensure network security. To do this:
- Use Azure DDoS protection to filter large-scale attacks before they cause a denial of service to end users.
- Use perimeter firewall with Azure Firewall to identify and alert on malicious attacks targeting your network.
Network layer:
At this layer, the focus is on restricting network connections between all resources to allow only what is required. Segment resources and use network-level controls to limit communication to only what is needed. By limiting connectivity, you reduce the risk of lateral movement throughout your network under attack. Use NSG to create rules on this layer for inbound and outbound communication. As a best practice:
- Limit communication between resources by segmenting your network and configuring access controls.
- Denied by default.
- Limit inbound internet access and, where appropriate, outbound.
- Enables secure connections to local networks.
Merge services:
Multiple Azure networking and security services can be used together to manage network security and provide enhanced layered protection. The following is an example of a composite service:
- Network Security Groups and Azure Firewall. Azure Firewall complements the network security group functionality. Together they provide better defense-in-depth network security. Network security groups provide distributed network-layer traffic filtering to limit traffic to resources within the virtual network in each subscription. Azure Firewall is a fully stateful, centralized network firewall-as-a-service that provides network and application-level protection across different subscriptions and virtual networks.
- Application Gateway WAF and Azure Firewall. WAF is a feature of Application Gateway that provides your web applications with centralized inbound protection against common exploits and vulnerabilities. Azure Firewall provides inbound protection for non-HTTP/S protocols (e.g., RDP, SSH, FTP), outbound network-level protection for all ports and protocols, and application-level protection for outbound HTTP/S. The two combined provide an extra layer of protection.
2. Check core identity services
When discussing authentication and access verification, there are two concepts that need to be understood:
- Authentication: Authentication is the process of establishing the identity of a person or service that wishes to access a resource; it involves the act of challenging a party to obtain legitimate credentials and provides the basis for creating secure topics for identity and access control.
- Authorization: Authorization is the process of establishing what level of access an authenticated person or service has. It specifies what data they are allowed to access and what can be done with it.
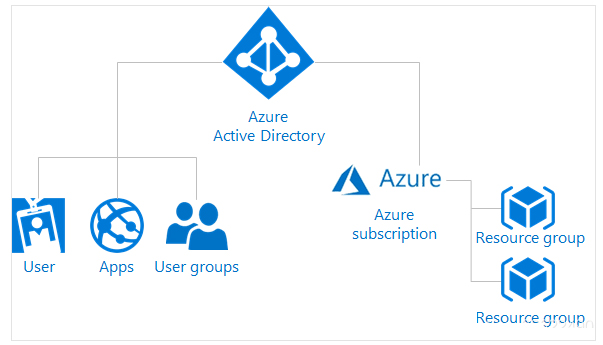
Azure Active Directory (AzureAD): Azure AD is a cloud-based identity and access management service that helps employees within an organization log in and access resources;
Internal resources: The corporate network and applications on the web, as well as any cloud applications developed within the organization
External resources: including Microsoft 365, Azure portal, and many other software and services (Saas) applications
Explore Azure Multi-Factor Authentication:
Identity verification requires two or more elements, which are divided into three categories:
- Something you know, like a password or the answer to a security question
- What you own, such as a device that accepts notification information or a device that generates tokens
- Characteristics you possess, such as biometrics, fingerprints or facial scans
Using multi-factor authentication (MFA) improves identity security by limiting the impact of credential exposure. For full authentication, for example, an attacker who has the user’s password would also need to have their phone or fingerprint. Authentication with just one factor is not enough and without MFA, attackers will be able to use these credentials to authenticate. MFA should be enabled whenever possible because MFA brings huge benefits to security.
Multi-factor authentication (MFA) is part of the following Azure service offerings:
- Azure Active Directory Premium Licensing. These licenses provide full-featured use of Azure Multi-function Authentication Service (cloud) or Azure Multi-function Authentication Server (on-premises).
- Multi-factor authentication for Microsoft 365. A subset of Azure multi-factor authentication features are available as part of a Microsoft 365 subscription.
- Azure Active Directory global administrator. Because global administrator accounts are so sensitive, these accounts can be protected using a subset of Azure’s multi-factor authentication capabilities.
3. View security tools and features
Security Center: A monitoring service that provides threat protection for all your services in Azure and on-premises
Azure Key Vault: Centralized cloud service for storing application secrets. Key Vault helps you control your application’s secrets by keeping them in a single, central location and providing secure access, permission control, and access logging capabilities.
Define Azure Advanced Threat Protection ATP: A cloud-based security solution that identifies, detects, and helps you investigate advanced threats, compromised identities, and malicious insider actions targeting your organization. Azure ATP detects known malicious attacks and techniques, security issues, and risks against your network.
Azure Advanced Threat Protection components:
- Azure Advanced Threat Protection (ATP) portal. Azure ATP has its own portal through which you can monitor and respond to suspicious activity. The Azure ATP portal allows you to create an Azure ATP instance and view data received from Azure ATP sensors. You can also use the portal to monitor, manage and investigate threats in your network environment.
- Azure Advanced Threat Protection (ATP) sensor. The Azure ATP sensor is installed directly on the domain controller. This sensor monitors domain controller traffic without the need for a dedicated server or configuration of port mirroring.
- Azure Advanced Threat Protection (ATP) cloud service. Azure ATP cloud service runs on Azure infrastructure and is currently deployed in the United States, Europe and Asia. Azure ATP cloud service is connected to Microsoft’s intelligent security graph.
4. Describe the Azure governance approach
Azure Policy: A service in Azure Policy for creating, assigning, and managing policies.
Azure policy creation and enforcement:
- Create a policy definition: Indicate what is to be evaluated and what actions to take; for example, you can block the deployment of a VM if it is exposed to a public IP address. You can also prevent hard disk usage when deploying VMs to control costs.
- Assign the definition to the resource scope: There are a lot of awkward translations on the official website. What I understand is to assign the definition you created in the previous step to the resource.
- View the policy evaluation results: When a condition is evaluated against your existing resources, the condition is marked as met or not met. You can review the results that do not comply with the policy and take any action required. Policy evaluation occurs approximately every hour, which means that if you make changes to the policy definition and create a policy assignment, it will re-evaluate your resources within an hour.
Role-Based Access Control RBAC: Provides fine-grained access management to Azure resources, allowing you to grant users only the permissions they need to perform their jobs. RBAC is provided free to all Azure subscribers.
Scenes to be used:
- Allow one user to manage the VMs in the subscription and another user to manage the virtual network.
- Allows the Database Administrators (DBA) group to manage SQL databases in a subscription.
- Allows users to manage all resources in a resource group such as VMs, websites, and subnets.
- Allows the application to access all resources in the resource group.
Here are some RBAC best practices:
- Using RBAC, you can separate responsibilities within your team and grant users only the access they need to perform their jobs. In addition to granting unrestricted permissions to everyone in an Azure subscription or resource, certain actions are only allowed at the scope level.
- When planning your access control policy, grant users the minimum level of privilege they need to do their jobs.
Define resource locks: Simply put, it is to prevent Azure resources from being deleted or modified by mistake. Can be set to “delete” lock and “read-only” lock.
Azure Blueprints: Allow you to reproducibly define a set of Azure resources that adhere to your organization’s standards, patterns, and requirements. Azure Blueprints enable development teams to leverage their knowledge of building within organizational compliance to quickly build and deploy new environments, using a set of built-in components to accelerate development and delivery.
5. Explore monitoring and reporting
Tags: Provide a logical taxonomy; each tag consists of a name and a value pair.
Label restrictions:
- Not all resource types support tags.
- You can have up to 50 tag name/value pairs per resource or resource group. Currently, storage accounts only support 15 tags, but in a future release, this limit will be increased to 50. If you need to apply more tags than the maximum allowed, use a JSON string as the tag value. A JSON string can contain many values that apply to a single tag name. A resource group can contain many resources, each with 50 tag name/value pairs.
- Tag names are limited to 512 characters and tag values are limited to 256 characters. For storage accounts, tag names are limited to 128 characters and tag values are limited to 256 characters.
- Virtual machines and virtual machine scale sets are limited to a total of 2048 characters for all tag names and values.
- Tags applied to a resource group are not inherited by resources in that resource group.
Azure Monitor: Provides a comprehensive solution to collect, analyze and execute telemetry from cloud and on-premises environments to maximize application availability and performance. It helps you understand the performance of your applications and proactively identify issues affecting them and the resources they depend on.
What data does Azure Monitor collect?
Azure Monitor can collect data from a variety of sources. You can think about monitoring an application’s data in layers, from the application, to any operating systems and services it relies on, all the way to the platform itself. Azure Monitor collects data from each of the following layers:
- Application monitoring data: Data about the performance and functionality of the code you write, regardless of its platform.
- Guest System Monitoring Data: Data about the operating system your application is running on. It can run in Azure, another cloud or on-premises.
- Azure Resource Monitoring Data: Data about Azure resource operations.
- Azure Subscription Monitoring Data: Data about the operation and management of your Azure subscription, as well as data about the health of Azure itself.
- Azure Tenant Monitoring Data: Data about the operation of tenant-level Azure services (such as Azure Active Directory).
Enable diagnostics
By enabling diagnostics and adding agents to compute the resource, you can extend the data you collect into the actual operation of the resource. Under resource settings you can enable diagnostics
- Enable guest-level monitoring
- Performance Counters: Collect performance data
- Event Log: Enable various event logs
- Crash dump: enable or disable
- Receiver: Send your diagnostic data to other services for more analysis
- Proxy: Configure proxy settings
Azure service health: This is an indicator that tells you the health status of Azure
Monitoring applications and services: Azure Monitor capabilities can be organized into four categories, these categories are: Analysis, Response, Visualization, and Integration.
6. Check privacy, compliance and data protection standards
Microsoft’s emphasis on this aspect can be reflected in four aspects:
- Microsoft Privacy Statement (explains which personal data is processed, how it is processed and for what purposes)
- Microsoft Trust Center (is a website resource that explains information and details on security, privacy, compliance, and transparency implemented and supported in all Microsoft cloud products and services.)
- Service Trust Portal STP (used to publish audit reports and other compliance-related information about Microsoft’s cloud services)
- Compliance Manager (workflow-based risk assessment that can track, assign, and verify the organization’s regulatory compliance activities related to Microsoft Professional Services and cloud services)
Part 4: Review, Pricing, Service Level Agreements and Lifecycle
1. Check your Azure subscription
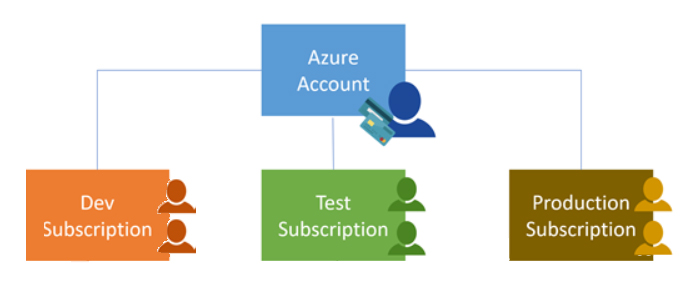
Azure Subscription: Using Azure requires an Azure subscription, which provides you with authenticated and authorized access to Azure products and services and allows you to provision resources. An Azure subscription is a logical unit of an Azure service linked to an Azure account, which is an identity in Azure Active Directory (Azure AD) or an Azure AD trusted directory. An account can have different subscriptions, each subscription has different billing models, and different access management policies need to be applied to it;
- Bill boundaries. This subscription type determines how your Azure account is billed using Azure. You can create multiple subscriptions for different billing requirements, and Azure will generate separate billing reports and invoices for each subscription so you can organize and manage your costs.
- Access control boundaries. Azure will apply access management policies at the subscription level, and you can create separate subscriptions to reflect different organizational structures. An example is, in an enterprise, you have different departments on which you apply different Azure subscription policies. This allows you to manage and control access to resources configured by users through specific subscriptions.
Management Groups: The organizational structure of resources in Azure has four levels: Management Groups, Subscriptions, Resource Groups, and Resources. The following diagram shows the relationship between these levels, i.e. the organizational hierarchy of individual objects
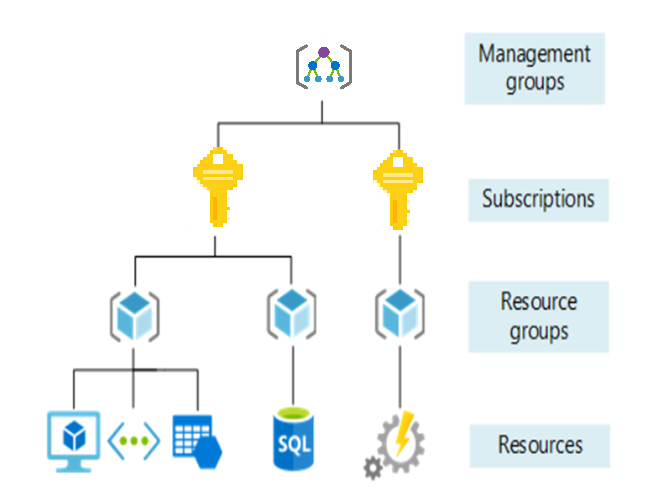
Management Groups: These containers help you manage access, policy, and compliance for multiple subscriptions. All subscriptions in a management group automatically inherit the conditions applied to that management group.
- A directory can support 10,000 management groups.
- The management group tree can support up to six levels of depth.
- This limit does not include Root or subscription levels.
- Only one parent can be supported per management group and subscription.
- Each management group can have many children.
Subscriptions: Subscriptions group together user accounts and the resources created by those user accounts. For each subscription, there are limits or quotas on the number of resources that can be created and used. Organizations can use subscriptions to manage costs, and resources created by users, teams, or projects.
Resource Group: A resource group is a logical container in which Azure resources (such as web applications, databases, and storage accounts) can be deployed and managed.
Resources: Resources are instances of services you create, such as virtual machines, storage, or SQL databases.
2. View plans and manage Azure costs
Several factors that affect cost:
- Usage meter: it is calculated based on the amount used for computer calculations, memory reading and writing, and network transmission;
- Resource Type: The cost is specific to the resource, so the usage of meter tracking and the number of meters related to resource management depends on the resource type;
- Services: Azure usage and billing cycles may vary between enterprise, Web Direct, and Cloud Solution Provider (CSP) customers. Some subscription types also include usage licenses, which affect the cost. The Azure team develops and delivers first-party products and services, while products and services from third-party vendors are available in the Azure Marketplace. A different billing structure applies to each category.
- Location: Because Azure covers the world, the cost of using services and resources of different scopes may vary between locations;
Pricing Calculator: This tool helps you estimate the cost of Azure products, it displays Azure products by categories, then selects the desired Azure product and configures it according to your specific requirements. Azure then provides a detailed estimate of the costs associated with your choices and configurations. Get new estimates from the pricing calculator by adding, removing, or reconfiguring selected products.
Total TCO Cost Calculator: A tool for estimating the cost savings you can achieve by migrating to Azure. Including servers, databases, storage, networking bandwidth, IT labor, hardware costs, software costs, electricity costs, virtualization costs, data center costs, network costs, etc.;
There are three steps to use this tool, define, adjust assumptions, and generate a report; click here to play with this tool
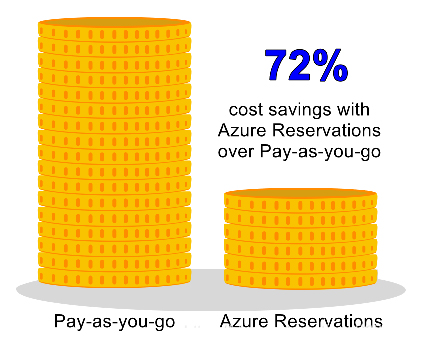
Azure Reservation: Provides discounted prices for certain Azure products and resources. To obtain the discount, you need to pay in advance to reserve the products and resources. You can pay for one or three years of virtual machines, SQL Database computes capacity, Azure Cosmos Database throughput, and other Azure resources. Azure subscriptions are only available to enterprise or CSP customers and pay-as-you-go subscriptions.
Learn about Azure Cost Management: An Azure product that provides a set of tools for monitoring, allocating, and optimizing Azure costs.
3. Azure Service Level Agreement SLA:
In a nutshell, system uptime; for each corresponding Azure product or service, typical SLA-specific performance target commitments range from 99.9% (“three nines”) to 99.99% (“four nines”). nine”). These goals can apply to performance criteria such as uptime or the response time of a service.
Some exam questions will ask you, if Azure’s promised SLA level is 99.9, which is correct. You can increase this level by adding availability zones or deploying on multiple virtual machines.
Two special service SLA levels:
- App Service Web Apps account for 99.95%.
- SQL database is 99.99%.
4. Azure preview features
- Private Preview – Azure Features are available for evaluation to certain Azure customers.
- Public Preview – All Azure customers can use Azure Functions for evaluation.
Remember, preview cannot be used in SLA, there has been this test question!
Take a screenshot of the preview function to get an impression:
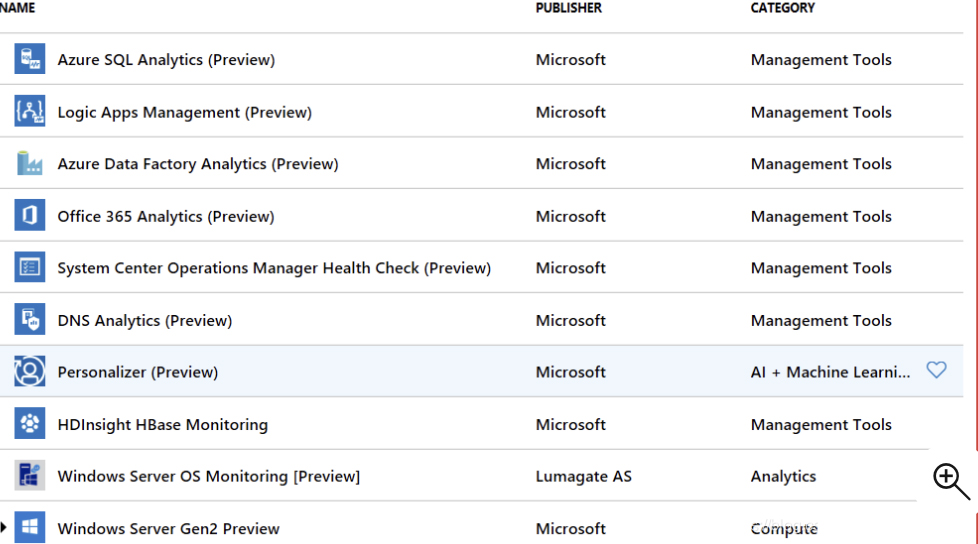
So far, the four major knowledge points of AZ-900 have been summarized. Below are some of the latest AZ-900 dumps exam questions, which contain the complete core exam content to help friends deeply understand the above content.
AZ-900 dumps exam questions online verification practice
| From | Number of exam questions | Type | Related certifications |
| Leads4Pass | 15 | Free | Azure, Fundamentals |
Question 1:
HOTSPOT
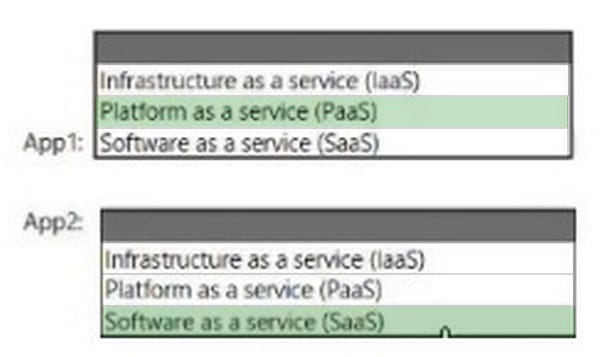
You plan to use Azure to host two apps named App1 and App2 The apps must meet the following requirements:
1.
You must be able to modify the code of App1
2.
Administrative effort to manage the operating system of App1 must be minimized.
3.
App2 must run interactively with the operating system of the server. Which type of cloud service should you use for each app?
Hot Area:
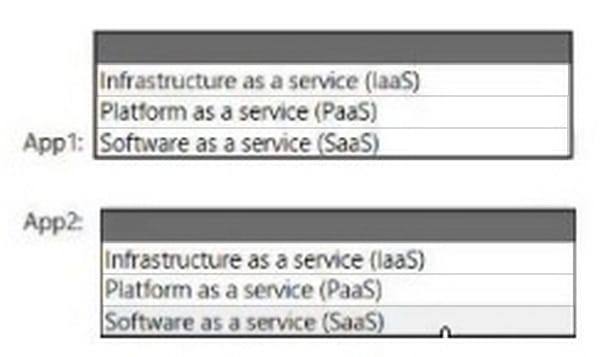
Correct Answer:
Question 2:
HOTSPOT
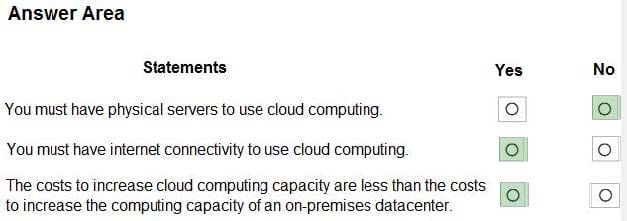
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
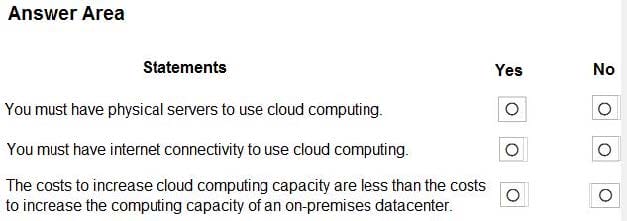
Correct Answer:
Explanation:
Box 1: No
A PaaS solution does not provide access to the operating system. The Azure Web Apps service provides an environment for you to host your web applications. Behind the scenes, the web apps are hosted on virtual machines running IIS.
However, you have no direct access to the virtual machine, the operating system or IIS.
Box 2: Yes
A PaaS solution that hosts web apps in Azure does provide the ability to scale the platform automatically. This is known as autoscaling. Behind the scenes, the web apps are hosted on virtual machines running IIS. Autoscaling means adding
more load balanced virtual machines to host the web apps.
Box 3: Yes
PaaS provides a framework that developers can build upon to develop or customize cloud-based applications. PaaS development tools can cut the time it takes to code new apps with pre-coded application components built into the platform,
such as workflow, directory services, security features, search and so on.
References:
https://azure.microsoft.com/en-gb/overview/what-is-paas/
Question 3:
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while
others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your Azure environment contains multiple Azure virtual machines.
You need to ensure that a virtual machine named VM1 is accessible from the Internet over HTTP.
Solution: You modify an Azure Traffic Manager profile.
Does this meet the goal?
A. Yes
B. No
Correct Answer: B
Azure Traffic Manager is a DNS-based load balancing solution. It is not used to ensure that a virtual machine named VM1 is accessible from the Internet over HTTP.
To ensure that a virtual machine named VM1 is accessible from the Internet over HTTP, you need to modify a network security group or Azure Firewall. In this question, we need to add a rule to a network security group or Azure Firewall to allow the connection to the virtual machine on port 80 (HTTP).
References: https://docs.microsoft.com/en-us/azure/traffic-manager/traffic-manager-overview
Question 4:
HOTSPOT For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point
Hot Area:

Correct Answer:

Question 5:
DRAG DROP
Match The cloud service models to the appropriate offerings.
To answer drag the appropriate model from the column on the left to its offering on the right. Each model may be used once, more than once, or not at all.
NOTE Each correct match is worth one point.
Select and Place:

Correct Answer:
Question 6:
This question requires that you evaluate the Bold text to determine if it is correct.
After you create a virtual machine, you need to modify the network security group (NSG) to allow connections from TCP port 8080 to the virtual machine.
Instructions: Review the underlined text. If it makes the statement correct, select “No change is needed”. If the statement is incorrect, select the answer choice that makes the statement correct.
A. No change is needed.
B. virtual network gateway.
C. virtual network
D. route table.
Correct Answer: A
Reference:
Question 7:
HOTSPOT
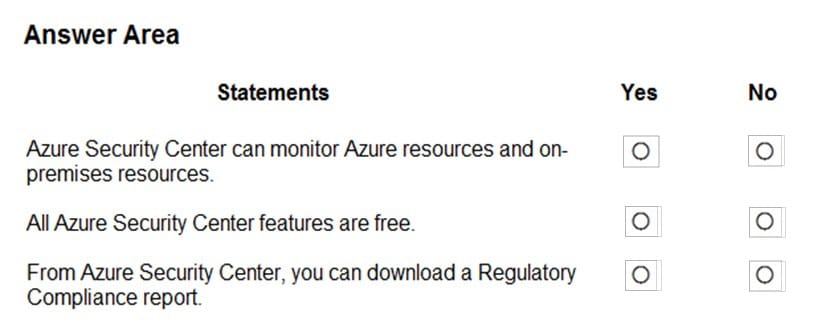
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
Correct Answer:
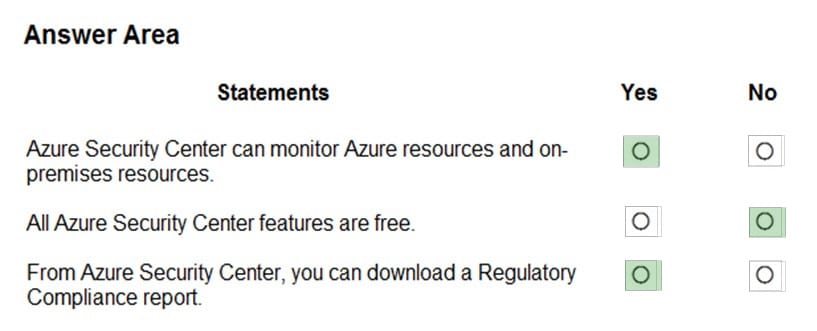
Box 1: Yes
Azure Security Center is a unified infrastructure security management system that strengthens the security posture of your data centers, and provides advanced threat protection across your hybrid workloads in the cloud – whether they\’re in
Azure or not – as well as on premises.
Box 2: No
Only two features: Continuous assessment and security recommendations, and Azure secure score, are free.
Box 3: Yes
The advanced monitoring capabilities in Security Center also let you track and manage compliance and governance over time. The overall compliance provides you with a measure of how much your subscriptions are compliant with policies
associated with your workload.
References:
https://docs.microsoft.com/en-us/azure/security-center/security-center-intro
Question 8:
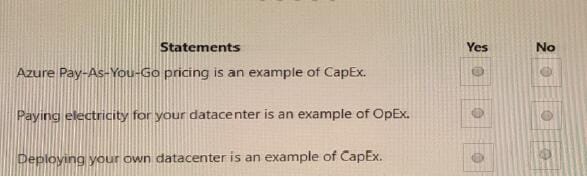
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
Hot Area:
Correct Answer:

Question 9:
Your company plans to deploy several web servers and several database servers to Azure.
You need to recommend an Azure solution to limit the types of connections from the web servers to the database servers.
What should you include in the recommendation?
A. network security groups (NSGs)
B. Azure Service Bus
C. a local network gateway
D. a route filter
Correct Answer: A
A network security group works like a firewall. You can attach a network security group to a virtual network and/or individual subnets within the virtual network. You can also attach a network security group to a network interface assigned to a virtual machine. You can use multiple network security groups within a virtual network to restrict traffic between resources such as virtual machines and subnets.
You can filter network traffic to and from Azure resources in an Azure virtual network with a network security group. A network security group contains security rules that allow or deny inbound network traffic to, or outbound network traffic from, several types of Azure resources.
References: https://docs.microsoft.com/en-us/azure/virtual-network/security-overview
Question 10:
A company has a Microsoft 365 subscription. Employees use personal devices to access company data in the cloud.
You need to restrict employees from copying data to personal OneDrive folders. What should you use?
A. Information Rights Management
B. Microsoft Azure Security Center
C. Office365 Advanced Threat Protection
D. Microsoft Endpoint Manager
Correct Answer: D
Reference: https://docs.microsoft.com/en-us/intune/app-protection-policy
Question 11:
You have an Azure subscription that contains an Azure virtual machine named VM1. VM1 runs a financial reporting app named App1 that does not support multiple active instances.
At the end of each month, CPU usage for VM1 peaks when App1 runs.
You need to create a scheduled runbook to increase the processor performance of VM1 at the end of each month.
What task should you include in the runbook?
A. Add the Azure Performance Diagnostics agent to VM1.
B. Modify the VM size property of VM1.
C. Add VM1 to a scale set.
D. Increase the vCPU quota for the subscription.
E. Add a Desired State Configuration (DSC) extension to VM1.
Correct Answer: E
Reference: https://docs.microsoft.com/en-us/azure/automation/automation-quickstart-dsc-configuration
Question 12:
You need to configure an Azure solution that meets the following requirements:
1.
Secures websites from attacks
2.
Generates reports that contain details of attempted attacks What should you include in the solution?
A. Azure Firewall
B. a network security group (NSG)
C. Azure Information Protection
D. DDoS protection
Correct Answer: D
DDoS is a type of attack that tries to exhaust application resources. The goal is to affect the application\’s availability and its ability to handle legitimate requests. DDoS attacks can be targeted at any endpoint that is publicly reachable through the internet.
Azure has two DDoS service offerings that provide protection from network attacks: DDoS Protection Basic and DDoS Protection Standard. DDoS Basic protection is integrated into the Azure platform by default and at no extra cost.
You have the option of paying for DDoS Standard. It has several advantages over the basic service, including logging, alerting, and telemetry. DDoS Standard can generate reports that contain details of attempted attacks as required in this question.
References: https://docs.microsoft.com/en-us/azure/security/fundamentals/ddos-best-practices
Question 13:
HOTSPOT
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
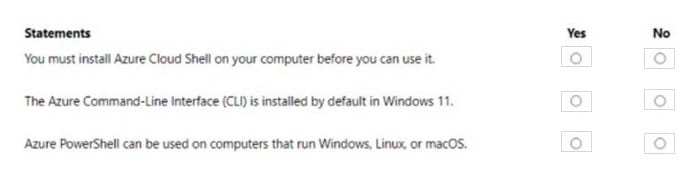
Correct Answer:
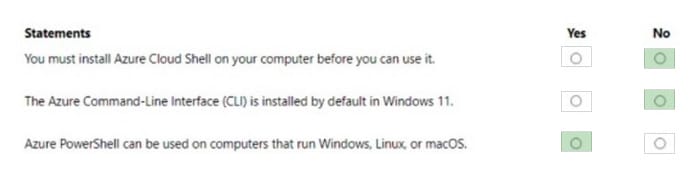
Question 14:
HOTSPOT
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
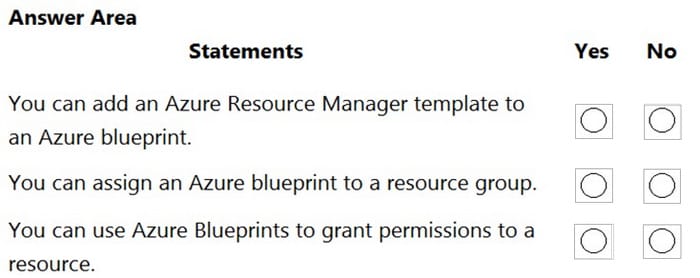
Correct Answer:
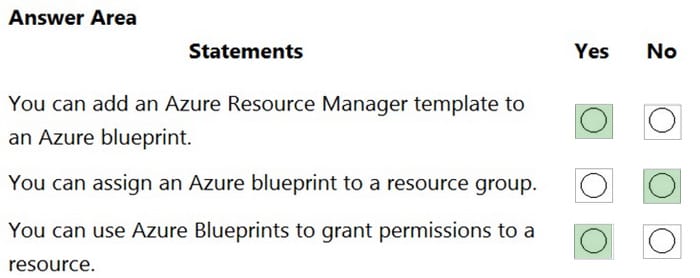
Reference: https://docs.microsoft.com/en-us/azure/governance/blueprints/overview
Question 15:
What should you use to evaluate whether your company\’s Azure environment meets regulatory requirements?
A. Azure Service Health
B. Azure Knowledge Center
C. Microsoft Defender for Cloud
D. Azure Advisor
Correct Answer: C
Microsoft Defender for Cloud helps streamline the process for meeting regulatory compliance requirements, using the regulatory compliance dashboard.
Reference: https://docs.microsoft.com/en-us/azure/defender-for-cloud/regulatory-compliance-dashboard
| More | learning method | From |
| 582 Q&A | PDF, VCE, PDF +VCE | https://www.leads4pass.com/az-900.html (AZ-900 dumps) |
Certificate summary
Passed the AZ-900 exam in 2024 and shared my experience. Generally speaking, all the content is not difficult to understand. The main reason is that it will be more obscure and difficult for people who have never been exposed to it. I went to the exam center to take the exam. I brought my ID card and For the driver’s license, all the questions are not very different from those in the question bank. After the test, the results can be printed out immediately. Microsoft will send the results to your mailbox after a while. I finished the 41 questions in the test in about 30 minutes. I was a little sloppy and passed the exam, mainly because I didn’t master the third part well! Here I recommend my learning route:
Leads4Pass az-900 dumps can roughly match the first 100 questions, and some of them are out of order later, but it does not affect the comparison of knowledge points to solve the questions!
Practice process:
- First go through all the basic concepts roughly and try your best to understand them. It doesn’t matter if you can’t remember them. The first time is mainly to go over them. If you can’t understand them at all, mark them and circle them.
- Start solving the questions directly. Go through them first and try to do it by yourself. If you have no idea at all, you should circle it. If you get it right, you should see if you can explain the reason for the answer. If you can explain the question, you can pass it directly.
- Understand the basic concepts that you don’t understand in step 1. Here you will definitely encounter questions that match the questions that have no ideas in step 2. Look at the concepts and problem-solving ideas at the same time. The key is to understand the ideas. Never change from the original.
- After completing steps 1, 2 and 3, you will have a macro understanding of the entire AZ-900 test points and what they roughly include; start to review the questions for the second time, and then circle the wrong questions to focus on understanding. Memorize it, and then you can take the exam with confidence and boldness

You may also like
Recent Posts
Categories
Microsoft Exam Dumps PDF Download
Microsoft Azure Exam PDF Free Download
- Microsoft az-104 PDF Free Download
- Microsoft az-120 PDF Free Download
- Microsoft az-140 PDF Free Download
- Microsoft az-204 PDF Free Download
- Microsoft az-220 PDF Free Download
- Microsoft az-305 PDF Free Download
- Microsoft az-400 PDF Free Download
- Microsoft az-500 PDF Free Download
- Microsoft az-700 PDF Free Download
- Microsoft az-800 PDF Free Download
- Microsoft az-801 PDF Free Download
Microsoft Data Exam PDF Free Download
- Microsoft AI-102 PDF Free Download
- Microsoft DP-100 PDF Free Download
- Microsoft DP-203 PDF Free Download
- Microsoft DP-300 PDF Free Download
- Microsoft DP-420 PDF Free Download
- Microsoft DP-600 PDF Free Download
Microsoft Dynamics 365 Exam PDF Free Download
- Microsoft MB-230 PDF Free Download
- Microsoft MB-240 PDF Free Download
- Microsoft MB-310 PDF Free Download
- Microsoft MB-330 PDF Free Download
- Microsoft MB-335 PDF Free Download
- Microsoft MB-500 PDF Free Download
- Microsoft MB-700 PDF Free Download
- Microsoft MB-800 PDF Free Download
- Microsoft MB-820 PDF Free Download
- Microsoft pl-100 PDF Free Download
- Microsoft pl-200 PDF Free Download
- Microsoft pl-300 PDF Free Download
- Microsoft pl-400 PDF Free Download
- Microsoft pl-500 PDF Free Download
- Microsoft pl-600 PDF Free Download
Microsoft 365 Exam PDF Free Download
- Microsoft MD-102 PDF Free Download
- Microsoft MS-102 PDF Free Download
- Microsoft MS-203 PDF Free Download
- Microsoft MS-700 PDF Free Download
- Microsoft MS-721 PDF Free Download
Microsoft Fundamentals Exam PDF Free Download
- Microsoft 62-193 PDF Free Download
- Microsoft az-900 PDF Free Download
- Microsoft ai-900 PDF Free Download
- Microsoft DP-900 PDF Free Download
- Microsoft MB-910 PDF Free Download
- Microsoft MB-920 PDF Free Download
- Microsoft pl-900 PDF Free Download
- Microsoft MS-900 PDF Free Download
Microsoft Certified Exam PDF Free Download
Recent Comments