
New SC-100 dumps: Covers complete Microsoft Cybersecurity Architect certification exam questions

The newly updated SC-100 dumps contains 105 exam questions and answers, provide both PDF and VCE learning solutions, and use lightweight learning solutions to help candidates quickly complete their target learning plans.
The Microsoft Cybersecurity Architect certification exam dumps contain all the core content:
Design a Zero Trust strategy and architecture (30-35%)
Evaluate Governance Risk Compliance (GRC) technical strategies and security operations strategies (10-15%)
Design security for infrastructure (10-15%)
Design a strategy for data and applications (15-20%)
Recommend security best practices and priorities (20-25%)
Candidates download SC-100 dumps provided by leads4pass:https://www.leads4pass.com/sc-100.html (Dumps PDF+VCE), Seriously practice 105 real and effective exam questions and answers to ensure 100% successfully pass Microsoft Cybersecurity Architect Certification Exam.
Exam SC-100: Microsoft Cybersecurity Architect Requirements:
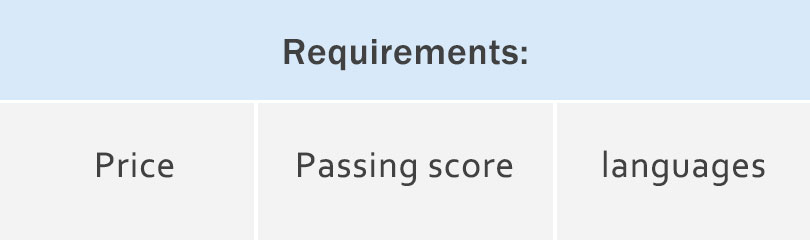
Candidates need to prepare a $165 registration fee for this exam. Passing score for this exam: 700, available in many languages: English, Japanese, Chinese (Simplified), Korean, German, French, Spanish, Portuguese (Brazil), Russian, Arabic (Saudi Arabia), Chinese (Traditional), Italian, Indonesian (Indonesia).
Provide a portion of the free SC-100 PDF download study:
https://drive.google.com/file/d/1ZJBHlBaov74rGXvnwWQUi6fuQKojHVDu/
Or, read the free SC-100 exam questions and answers online:
| Number of exam questions | Exam name | From | Release time |
| 13 | Microsoft Cybersecurity Architect | leads4pass | Nov 07, 2022 |
NEW QUESTION 1:
A customer has a hybrid cloud infrastructure that contains a Microsoft 365 E5 subscription and an Azure subscription.
All the on-premises servers in the perimeter network are prevented from connecting directly to the internet.
The customer recently recovered from a ransomware attack.
The customer plans to deploy Microsoft Sentinel.
You need to recommend configurations to meet the following requirements:
Ensure that the security operations team can access the security logs and the operation logs.
Ensure that the IT operations team can access only the operations logs, including the event logs of the servers in the perimeter network.
Which two configurations can you include in the recommendation? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
A. Configure Azure Active Directory (Azure AD) Conditional Access policies.
B. Use the Azure Monitor agent with the multi-homing configuration.
C. Implement resource-based role-based access control (RBAC) in Microsoft Sentinel.
D. Create a custom collector that uses the Log Analytics agent.
Correct Answer: A
NEW QUESTION 2:
Your company has an on-premises network and an Azure subscription.
The company does NOT have a Site-to-Site VPN or an ExpressRoute connection to Azure.
You are designing the security standards for Azure App Service web apps. The web apps will access Microsoft SQL Server databases on the network.
You need to recommend security standards that will allow web apps to access the databases. The solution must minimize the number of open internet-accessible endpoints to the on-premises network.
What should you include in the recommendation?
A. a private endpoint
B. hybrid connections
C. virtual network NAT gateway integration
D. virtual network integration
Correct Answer: C
NEW QUESTION 3:
Your company is developing a serverless application in Azure that will have the architecture shown in the following exhibit.
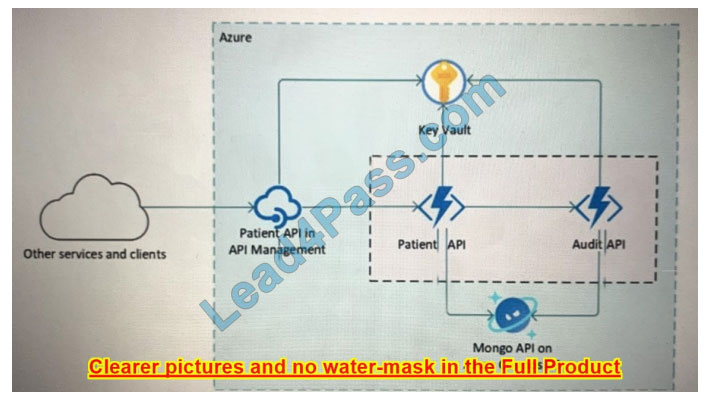
You need to recommend a solution to isolate the compute components on an Azure virtual network.
What should you include in the recommendation?
A. Azure Active Directory (Azure AD) enterprise applications
B. an Azure App Service Environment (ASE)
C. Azure service endpoints
D. an Azure Active Directory (Azure AD) application proxy
Correct Answer: B
NEW QUESTION 4:
You have an on-premises network that has several legacy applications. The applications perform LDAP queries against an existing directory service. You are migrating the on-premises infrastructure to a cloud-only infrastructure.
You need to recommend an identity solution for the infrastructure that supports the legacy applications.
The solution must minimize the administrative effort to maintain the infrastructure.
Which identity service should you include in the recommendation?
A. Azure Active Directory Domain Services (Azure AD DS)
B. Azure Active Directory (Azure AD) B2C
C. Azure Active Directory (Azure AD)
D. Active Directory Domain Services (AD DS)
Correct Answer: A
NEW QUESTION 5:
You need to recommend a multi-tenant and hybrid security solution that meets the business requirements and the hybrid requirements. What should you recommend? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:

Correct Answer:

NEW QUESTION 6:
33 – (Topic 3)
Your company is moving all on-premises workloads to Azure and Microsoft 365. You need to design a security orchestration, automation, and response (SOAR) strategy in Microsoft Sentinel that meets the following requirements:
Minimizes manual intervention by security operation analysts
Supports Waging alerts within Microsoft Teams channels
What should you include in the strategy?
A. data connectors
B. playbooks
C. workbooks
D. KQL
Correct Answer: C
NEW QUESTION 7:
Your company has on-premises Microsoft SQL Server databases.
The company plans to move the databases to Azure.
You need to recommend a secure architecture for the databases that will minimize operational requirements for patching and protect sensitive data by using dynamic data masking. The solution must minimize costs.
What should you include in the recommendation?
A. Azure SQL Managed Instance
B. Azure Synapse Analytics dedicated SQL pools
C. Azure SQL Database
D. SQL Server on Azure Virtual Machines
Correct Answer: D
NEW QUESTION 8:
You need to recommend a solution to meet the security requirements of the InfraSec group. What should you use to delegate access?
A. a subscription
B. a custom role-based access control (RBAC) role
C. a resource group
D. a management group
Correct Answer: D
NEW QUESTION 9:
You need to recommend an identity security solution for the Azure AD tenant of Litware.
The solution must meet the identity requirements and the regulatory compliance requirements.
What should you recommend? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
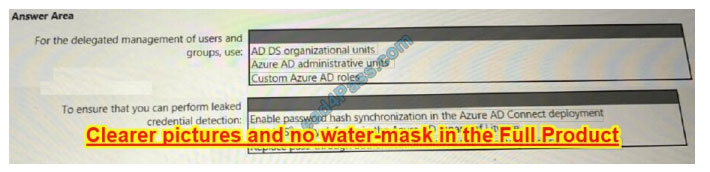
Correct Answer:
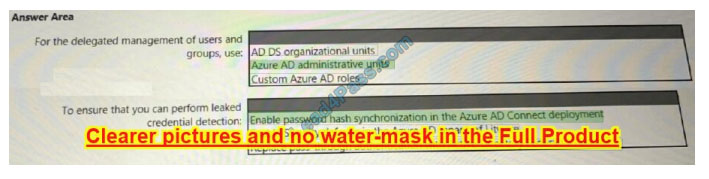
NEW QUESTION 10:
You are designing the security standards for a new Azure environment.
You need to design a privileged identity strategy based on the Zero Trust model.
Which framework should you follow to create the design?
A. Enhanced Security Admin Environment (ESAE)
B. Microsoft Security Development Lifecycle (SDL)
C. Rapid Modernization Plan (RaMP)
D. Microsoft Operational Security Assurance (OSA)
Correct Answer: A
NEW QUESTION 11:
You have a Microsoft 365 E5 subscription.
You are designing a solution to protect confidential data in Microsoft SharePoint Online sites that contain more than one million documents.
You need to recommend a solution to prevent Personally Identifiable Information (Pll) from being shared.
Which two components should you include in the recommendation? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
A. data loss prevention (DLP) policies
B. sensitivity label policies
C. retention label policies
D. eDiscovery cases
Correct Answer: AD
NEW QUESTION 12:
Your company is developing a new Azure App Service web app. You are providing design assistance to verify the security of the web app.
You need to recommend a solution to test the web app for vulnerabilities such as insecure server configurations, cross-site scripting (XSS), and SQL injection.
What should you include in the recommendation?
A. interactive application security testing (IAST)
B. static application security testing (SAST)
C. runtime application se/f-protection (RASP)
D. dynamic application security testing (DAST)
Correct Answer: A
NEW QUESTION 13:
You have an Azure subscription that has Microsoft Defender for Cloud enabled. You have an Amazon Web Services (AWS) implementation.
You plan to extend the Azure security strategy to the AWS implementation. The solution will NOT use Azure Arc.
Which three services can you use to provide security for the AWS resources? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
A. Azure Active Directory (Azure AD) Privileged Identity Management (PIM)
B. Azure Active Directory (Azure AD) Conditional Access
C. Microsoft Defender for servers
D. Azure Policy
E. Microsoft Defender for Containers
Correct Answer: BE
…
Covers complete Microsoft Cybersecurity Architect certification exam questions New SC-100 dumps can be downloaded from leads4pass: https://www.leads4pass.com/sc-100.html.
Covers complete core exam questions and answers using PDF or VCE learning solutions to solve target exams welcomes candidates to use SC-100 dumps and guarantees 100% success in target exams.
By the way, provide the above SC-100 exam questions and answers for online download:https://drive.google.com/file/d/1ZJBHlBaov74rGXvnwWQUi6fuQKojHVDu/
You may also like
Recent Posts
Categories
Microsoft Exam Dumps PDF Download
Microsoft Azure Exam PDF Free Download
- Microsoft az-104 PDF Free Download
- Microsoft az-120 PDF Free Download
- Microsoft az-140 PDF Free Download
- Microsoft az-204 PDF Free Download
- Microsoft az-220 PDF Free Download
- Microsoft az-305 PDF Free Download
- Microsoft az-400 PDF Free Download
- Microsoft az-500 PDF Free Download
- Microsoft az-700 PDF Free Download
- Microsoft az-800 PDF Free Download
- Microsoft az-801 PDF Free Download
Microsoft Data Exam PDF Free Download
- Microsoft AI-102 PDF Free Download
- Microsoft DP-100 PDF Free Download
- Microsoft DP-203 PDF Free Download
- Microsoft DP-300 PDF Free Download
- Microsoft DP-420 PDF Free Download
- Microsoft DP-600 PDF Free Download
Microsoft Dynamics 365 Exam PDF Free Download
- Microsoft MB-230 PDF Free Download
- Microsoft MB-240 PDF Free Download
- Microsoft MB-310 PDF Free Download
- Microsoft MB-330 PDF Free Download
- Microsoft MB-335 PDF Free Download
- Microsoft MB-500 PDF Free Download
- Microsoft MB-700 PDF Free Download
- Microsoft MB-800 PDF Free Download
- Microsoft MB-820 PDF Free Download
- Microsoft pl-100 PDF Free Download
- Microsoft pl-200 PDF Free Download
- Microsoft pl-300 PDF Free Download
- Microsoft pl-400 PDF Free Download
- Microsoft pl-500 PDF Free Download
- Microsoft pl-600 PDF Free Download
Microsoft 365 Exam PDF Free Download
- Microsoft MD-102 PDF Free Download
- Microsoft MS-102 PDF Free Download
- Microsoft MS-203 PDF Free Download
- Microsoft MS-700 PDF Free Download
- Microsoft MS-721 PDF Free Download
Microsoft Fundamentals Exam PDF Free Download
- Microsoft 62-193 PDF Free Download
- Microsoft az-900 PDF Free Download
- Microsoft ai-900 PDF Free Download
- Microsoft DP-900 PDF Free Download
- Microsoft MB-910 PDF Free Download
- Microsoft MB-920 PDF Free Download
- Microsoft pl-900 PDF Free Download
- Microsoft MS-900 PDF Free Download
Microsoft Certified Exam PDF Free Download
Recent Comments