Microsoft 365 Security Administration Certification Exam MS-500 dumps Q&A
MS-500 dumps exam questions and answers are the best preparation for the Microsoft 365 Security Administration certification exam.
MS-500 dumps contain 249 latest exam questions and answers. We screened important exam questions and added new valid exam questions, which are verified by subject matter experts. They are real and effective, and you are guaranteed to successfully pass the Microsoft 365 Security Administration certification.
What is an MS-500 Exam Dumps?
MS-500 Dumps: In fact, it is short for containing PDf files and the VCE learning engine. The leads4pass MS-500 dumps page https://www.leads4pass.com/ms-500.html, contains the real MS-500 exam Dumps, in the true sense of the requirements of the candidate, And guarantees your first pass in the Microsoft 365 Security Administration certification exam.
Microsoft 365 Security Administration MS-500 Certification Exam Preparation: MS-500 Exam Details, MS-500 Exam Practice
MS-500 Exam Details:
Vendor: Microsoft
Exam Code: MS-500
Exam Name: Microsoft 365 Security Administration
Certification: Microsoft 365 Certified: Security Administrator Associate
Languages: English, Japanese, Chinese (Simplified), Korean, German, French, Spanish, Portuguese (Brazil), Russian, Arabic (Saudi Arabia), Chinese (Traditional), Italian
Price: $165 USD
Duration: 120 mins
Number of Questions: 40-60
Passing score: 700/1000
MS-500 Online Exam Practice:
Share time: June 7, 2022
QUESTION 1:
An administrator plans to deploy several Azure Advanced Threat Protection (ATP) sensors.
You need to provide the administrator with the Azure information required to deploy the sensors.
What information should you provide?
A. an Azure Active Directory Authentication Library (ADAL) token
B. the public key
C. the access key
D. the URL of the Azure ATP admin center
Correct Answer: D
Reference: https://docs.microsoft.com/en-us/azure-advanced-threat-protection/workspace-portal
QUESTION 2:
You have an Azure Sentinel workspace that has an Azure Active Directory (Azure AD) connector and a Microsoft Office 365 connector. You need to assign built-in role-based access control (RBAC) roles to achieve the following tasks:
1. Create and run playbooks.
2. Manage incidents.
The solution must use the principle of least privilege.
Which two roles should you assign? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
A. Automation Operator
B. Azure Sentinel responder
C. Automation Runbook Operator
D. Azure Sentinel contributor
E. Logic App contributor
Correct Answer: DE
Reference: https://docs.microsoft.com/en-us/azure/sentinel/roles
QUESTION 3:
Your company uses Microsoft Azure Advanced Threat Protection (ATP).
You enable the delayed deployment of updates for an Azure ATP sensor named Sensor1.
How long after the Azure ATP cloud service is updated will Sensor1 be updated?
A. 7 days
B. 24 hours
C. 1 hour
D. 48 hours
E. 12 hours
Correct Answer: B
Note: The delay period was 24 hours. In ATP release 2.62, the 24-hour delay period has been increased to 72 hours.
QUESTION 4:
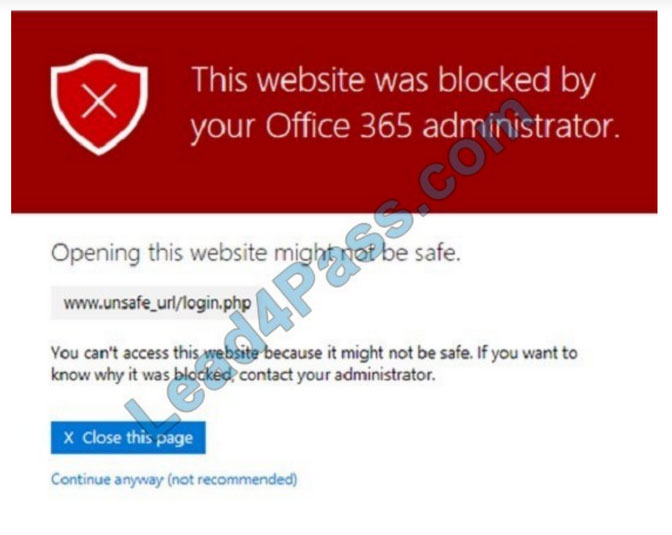
A user phones to complain that his browser is not allowing him to visit a URL that is normally used for business saying that “This website was blocked by your O ce 365 administrators.” as in the exhibit.

You know that your M365 security policies were recently updated. Where would you start your investigation?
A. Microsoft Defender ATP
B. Azure ATP
C. Office ATP
D. Microsoft Secure Score
Correct Answer: C
URL blocking is part of Office365 ATP Safe Links Reference: https://docs.microsoft.com/en-
us/microsoft-365/security/office-365-security/atp-safe-links-warning-pages
QUESTION 5:
How do you integrate Office365 ATP with MD-ATP? Each option is a complete solution. (Choose two.)
A. There is no integration between 0365 ATP and MD-ATP
B. Go to protection.office.com, threat management, explorer, WDATP settings, and enable
C. Go to securitycenter.windows.com, settings, advanced features, Office 365 threat intelligence connection, enable
D. Go to security.microsoft.com, threat management, explorer, WDATP settings, and enable
Correct Answer: BC
Office365 ATP is referred to as Office365 threat intelligence in the integration settings. You can enable the integration between the two products from either side. You don\’t have to configure the integration on both sides. This is true for Office365 ATP and MD-ATP, but not for all three ATP products.
Be sure to understand which ATP products can be integrated with each other and when you would need to do so.
Reference: https://docs.microsoft.com/en-za/microsoft-365/security/office-365-security/integrate-office-365-ti-with-wdatp#to-integrate-office-365-atpwith-microsoft-defender-atp https://docs.microsoft.com/en-za/microsoft-365/security/office-365-security/office-365-ti
QUESTION 6:
You need to identify which Microsoft platforms provide hybrid capabilities for migrating from an on-premises deployment. Which two platforms provide hybrid capabilities for migration? Each correct answer provides a complete solution. (Choose two.) NOTE: Each correct selection is worth one point.
A. Microsoft Skype for Business
B. Microsoft Yammer
C. Microsoft Exchange
D. Microsoft Teams
Correct Answer: AC
QUESTION 7:
Which of the following tools will you use to manage regulatory compliance within the shared responsibility model of the cloud?
A. Service Trust Portal
B. Compliance Manager
C. Trust Center
D. Azure Security Center
E. Microsoft Compliance Portal
Correct Answer: B
Both the compliance manager and the trust center are components of the service trust portal. Each of them has a different purpose. See the document link for details.

QUESTION 8:
You need to ensure that all links to malware.contoso.com within documents stored in Microsoft Office 365 are blocked when the documents are accessed from Office 365 ProPlus applications.
To complete this task, sign in to the Microsoft 365 admin center.
Correct Answer: See below.
1. After signing in to the Microsoft 365 admin center, navigate to Threat management, choose Policy > Safe Links.
2. In the Policies that apply to the entire organization section, select Default, and then choose Edit (the Edit button resembles a pencil).
3. In the Block the following URLs section, add the malware.contoso.com link.
4. In the Settings that apply to content except email section, select all the options.
5. Choose Save.

QUESTION 9:
Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.
Hot Area:
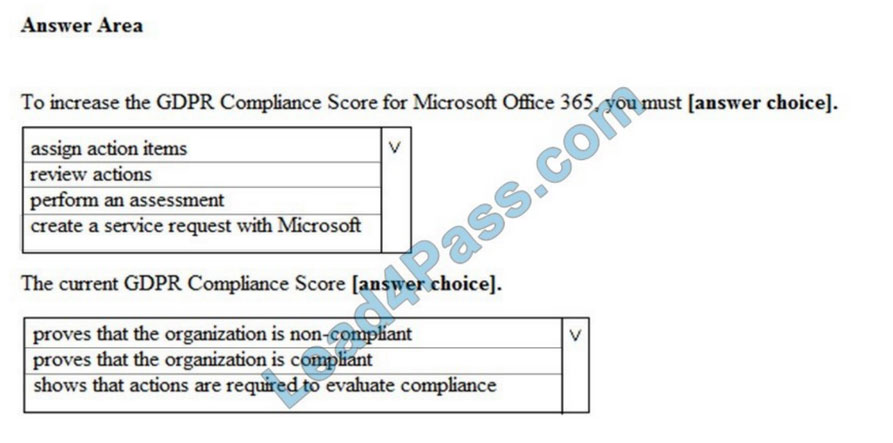
Correct Answer:
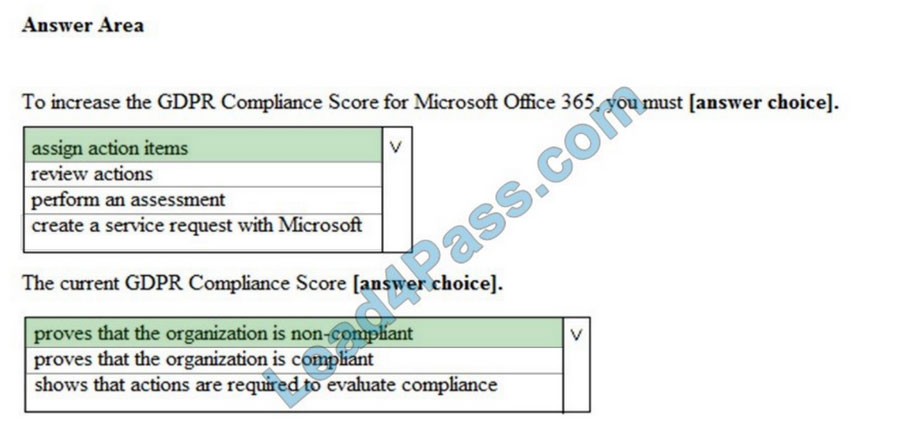
QUESTION 10:
HOTSPOT
You have a Microsoft 365 subscription that contains the users shown in the following table.
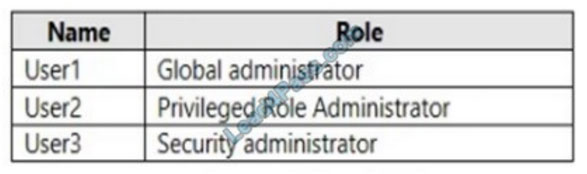
You implement Azure Active Directory (Azure AD) Privileged Identity Management (PIM).
From PIM, you review the Application Administrator role and discover the users shown in the following table.
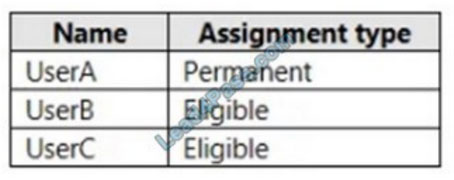
The Application Administrator role is configured to use the following settings in PIM:
1.
Maximum activation duration: 1 hour
2.
Notifications: Disable
3.
Incident/Request ticket: Disable
4.
Multi-Factor Authentication: Disable
5.
Require approval: Enable
6.
Selected approver: No results
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:

Correct Answer:

QUESTION 11:
You have a hybrid Microsoft 365 deployment that contains the Windows 10 devices shown in the following table. You assign a Microsoft Endpoint Manager disk encryption policy that automatically and silently enables BitLocker Drive Encryption (BitLocker) on all the devices. Which devices will have BitLocker enabled?
A. Device1, Device2, and Device3
B. Device2 only
C. Device1 and Device2 only
D. Device2 and Device3 only
Correct Answer: B
To silently enable BitLocker, the device must be Azure AD Joined or Hybrid Azure AD Joined and the device must contain TPM (Trusted Platform Module) 2.0. Incorrect Answers:
A: Device1 is not Azure AD Joined or Hybrid Azure AD Joined, and the TPM version on Device3 is only 1.3. To silently enable BitLocker, the device must be Azure AD Joined or Hybrid Azure AD Joined and the device must contain TPM (Trusted Platform Module) 2.0.
C: Device1 is not Azure AD Joined or Hybrid Azure AD Joined. To silently enable BitLocker, the device must be Azure AD Joined or Hybrid Azure AD Joined.
D: The TPM version on Device3 is only 1.3. To silently enable BitLocker, the device must contain TPM (Trusted Platform Module) 2.0.
Reference:
https://docs.microsoft.com/en-us/mem/intune/protect/encrypt-devices
QUESTION 12:
You have implemented Azure AD Connect for your organization. You have made some changes to user accounts in your local Active Directory and notice that these changes have not yet synchronized to Azure. What is the PS command to force an Azure AD Connect sync?
A. Start-ADSyncSyncCycle-PolicyType Delta
B. Start-ADSyncSyncCycle-PolicyType Initial
C. Get-ADSyncScheduler
D. Set-MsolDirSyncFeature-Feature SynchronizeUpnForManagedUsers-Enable $true
Correct Answer: A
Reference:
https://techcommunity.microsoft.com/t5/itops-talk-blog/powershell-basics-how-to-force-azuread-connect-to-sync/ba-p/887043
https://docs.microsoft.com/en-us/azure/active-directory/hybrid/how-to-connect-sync-whatis https://docs.microsoft.com/en-us/azure/activedirectory/ hybrid/how-to-connect-syncservice-features
QUESTION 13:
NOTE: This question is a part of a series of questions that present the same scenario. For each of the following statements, select the best response(s) to the question or statement below. Each answer is worth one point. After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. Your company\’s head of IT Security has instructed you to put a continual privileged access review system in place. He requires that all privileged accounts be reviewed every seven days. Users with administrative privileges must self-assess their access, however, if an administrator doesn\’t respond within three days of receiving such a request, privileged access must be removed. Where would you configure what happens if a reviewer doesn\’t respond to the request?
A. Upon completion settings
B. Advanced settings
C. Duration
D. Review role membership
Correct Answer: A
Upon completion settings allow you to specify what happens when a user doesn\’t respond to the assessment.
Reference: https://docs.microsoft.com/en-us/azure/active-directory/privileged-identity-management/pim-how-to-perform-security-review https://docs.microsoft.com/en-us/azure/active-directory/privileged-identity-management/pim-how-to-start-securityreview
……
[Google Drive] MS-500 Exam Practice Questions Online Download: https://drive.google.com/file/d/1cRbYoub0dtg9g5sM7PSI7FOKKG7H5TDT/
249 MS-500 Dumps exam questions and answers are available online: click to view
You may also like
Recent Posts
Categories
Microsoft Exam Dumps PDF Download
Microsoft Azure Exam PDF Free Download
- Microsoft az-104 PDF Free Download
- Microsoft az-120 PDF Free Download
- Microsoft az-140 PDF Free Download
- Microsoft az-204 PDF Free Download
- Microsoft az-220 PDF Free Download
- Microsoft az-305 PDF Free Download
- Microsoft az-400 PDF Free Download
- Microsoft az-500 PDF Free Download
- Microsoft az-700 PDF Free Download
- Microsoft az-800 PDF Free Download
- Microsoft az-801 PDF Free Download
Microsoft Data Exam PDF Free Download
- Microsoft AI-102 PDF Free Download
- Microsoft DP-100 PDF Free Download
- Microsoft DP-203 PDF Free Download
- Microsoft DP-300 PDF Free Download
- Microsoft DP-420 PDF Free Download
- Microsoft DP-600 PDF Free Download
Microsoft Dynamics 365 Exam PDF Free Download
- Microsoft MB-230 PDF Free Download
- Microsoft MB-240 PDF Free Download
- Microsoft MB-310 PDF Free Download
- Microsoft MB-330 PDF Free Download
- Microsoft MB-335 PDF Free Download
- Microsoft MB-500 PDF Free Download
- Microsoft MB-700 PDF Free Download
- Microsoft MB-800 PDF Free Download
- Microsoft MB-820 PDF Free Download
- Microsoft pl-100 PDF Free Download
- Microsoft pl-200 PDF Free Download
- Microsoft pl-300 PDF Free Download
- Microsoft pl-400 PDF Free Download
- Microsoft pl-500 PDF Free Download
- Microsoft pl-600 PDF Free Download
Microsoft 365 Exam PDF Free Download
- Microsoft MD-102 PDF Free Download
- Microsoft MS-102 PDF Free Download
- Microsoft MS-203 PDF Free Download
- Microsoft MS-700 PDF Free Download
- Microsoft MS-721 PDF Free Download
Microsoft Fundamentals Exam PDF Free Download
- Microsoft 62-193 PDF Free Download
- Microsoft az-900 PDF Free Download
- Microsoft ai-900 PDF Free Download
- Microsoft DP-900 PDF Free Download
- Microsoft MB-910 PDF Free Download
- Microsoft MB-920 PDF Free Download
- Microsoft pl-900 PDF Free Download
- Microsoft MS-900 PDF Free Download
Microsoft Certified Exam PDF Free Download
Recent Comments