[April 2025]AZ-500 dumps update from Leads4Pass
Why can an AZ-500 dumps help me pass the Microsoft Azure Security Technologies exam successfully?
AZ-500 dumps are carefully collected by a number of IT certification experts based on the Microsoft Azure Security Technologies certification core exam questions, and then compiled the most effective exam questions and answers, and share analysis methods, The most effective material for preparing candidates for the AZ-500 Microsoft Azure Security Technologies exam.
You can download the AZ-500 dumps from this site:https://www.leads4pass.com/az-500.html, find the latest updated 364 questions and answers for the AZ-500 exam, as well as two study modes, PDF and VCE, to help you complete the AZ-500 Microsoft Azure Security Technologies exam perfectly and pass it successfully AZ-500 Microsoft Azure Security Technologies exam.
[Practice Test] We also share some AZ-500 free dumps to help you practice online
The questions for AZ-500 were last updated on April 25, 2022.
Viewing questions 1-15 out of 364 questions:
Question 1:
You need to meet the technical requirements for VNetwork1. What should you do first?
A. Create a new subnet on VNetwork1.
B. Remove the NSGs from Subnet11 and Subnet13.
C. Associate an NSG to Subnet12.
D. Configure DDoS protection for VNetwork1.
Correct Answer: A
From scenario: Deploy Azure Firewall to VNetwork1 in Sub2.
The azure firewall needs a dedicated subnet named AzureFirewallSubnet.
References:
https://docs.microsoft.com/en-us/azure/firewall/tutorial-firewall-deploy-portal
Question 2:
You need to ensure that User2 can implement PIM. What should you do first?
A. Assign User2 the global administrator role.
B. Configure authentication methods for contoso.com.
C. Configure the identity secure score for contoso.com.
D. Enable multi-factor authentication (MFA) for User2.
Correct Answer: A
To start using PIM in your directory, you must first enable PIM.
1. Sign in to the Azure portal as a Global Administrator of your directory.
You must be a Global Administrator with an organizational account (for example, @yourdomain.com), not a Microsoft account (for example, @outlook.com), to enable PIM for a directory.
Scenario: Technical requirements include: Enable Azure AD Privileged Identity Management (PIM) for contoso.com
References:
Question 3:
You need to ensure that users can access VM0. The solution must meet the platform protection requirements. What should you do?
A. Move VM0 to Subnet1.
B. On Firewall, configure a network traffic filtering rule.
C. Assign RT1 to AzureFirewallSubnet.
D. On Firewall, configure a DNAT rule.
Correct Answer: A
Explanation:
Azure Firewall has the following known issue:
Conflict with Azure Security Center (ASC) Just-in-Time (JIT) feature.
If a virtual machine is accessed using JIT and is in a subnet with a user-defined route that points to Azure Firewall as a default gateway, ASC JIT doesn\’t work. This is a result of asymmetric routing – a packet comes in via the virtual machine
public IP (JIT opened the access), but the return path is via the firewall, which drops the packet because there is no established session on the firewall.
Solution: To work around this issue, place the JIT virtual machines on a separate subnet that doesn\’t have a user-defined route to the firewall.
Scenario:
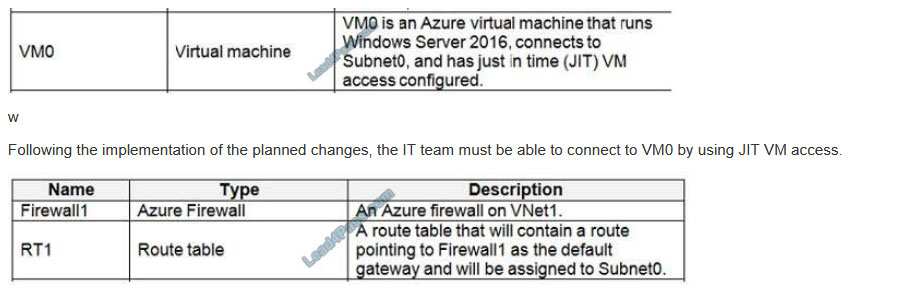
References: https://docs.microsoft.com/en-us/azure/firewall/overview
Question 4:
You need to configure WebApp1 to meet the data and application requirements.
Which two actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
A. Upload a public certificate.
B. Turn on the HTTPS Only protocol setting.
C. Set the Minimum TLS Version protocol setting to 1.2.
D. Change the pricing tier of the App Service plan.
E. Turn on the Incoming client certificates protocol setting.
Correct Answer: AC
A: To configure Certificates for use in Azure Websites Applications you need to upload a public Certificate.
C: Over time, multiple versions of TLS have been released to mitigate different vulnerabilities. TLS 1.2 is the most current version available for apps running on Azure App Service. Incorrect Answers:
B: We need to support the HTTP URL as well. Note:

References: https://docs.microsoft.com/en-us/azure/app-service/app-service-web-configure-tls-mutual-auth
Question 5:
You need to meet the identity and access requirements for Group1. What should you do?
A. Add a membership rule to Group1.
B. Delete Group1. Create a new group named Group1 that has a membership type of Office 365. Add users and devices to the group.
C. Modify the membership rule of Group1.
D. Change the membership type of Group1 to Assigned. Create two groups that have dynamic memberships. Add the new groups to Group1.
Correct Answer: B
Incorrect Answers:
A, C: You can create a dynamic group for devices or for users, but you can\’t create a rule that contains both users and devices.
D: For the assigned group, you can only add individual members.
Scenario:
Litware identifies the following identity and access requirements: All San Francisco users and their devices must be members of Group1.
The tenant currently contains this group:
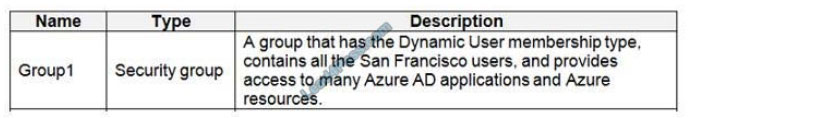
References: https://docs.microsoft.com/en-us/azure/active-directory/users-groups-roles/groups-dynamic-membership
Question 6:
SIMULATION
The developers at your company plan to create a web app named App10598168 and to publish the app to https://www.contoso.com.
You need to perform the following tasks:
1.
Ensure that App10598168 is registered to Azure Active Directory (Azure AD).
2.
Generate a password for App10598168.
To complete this task, sign in to the Azure portal.
A. See the below.
Correct Answer: A
Step 1: Register the Application
1.
Sign in to your Azure Account through the Azure portal.
2.
Select Azure Active Directory.
3.
Select App registrations.
4.
Select New registration.
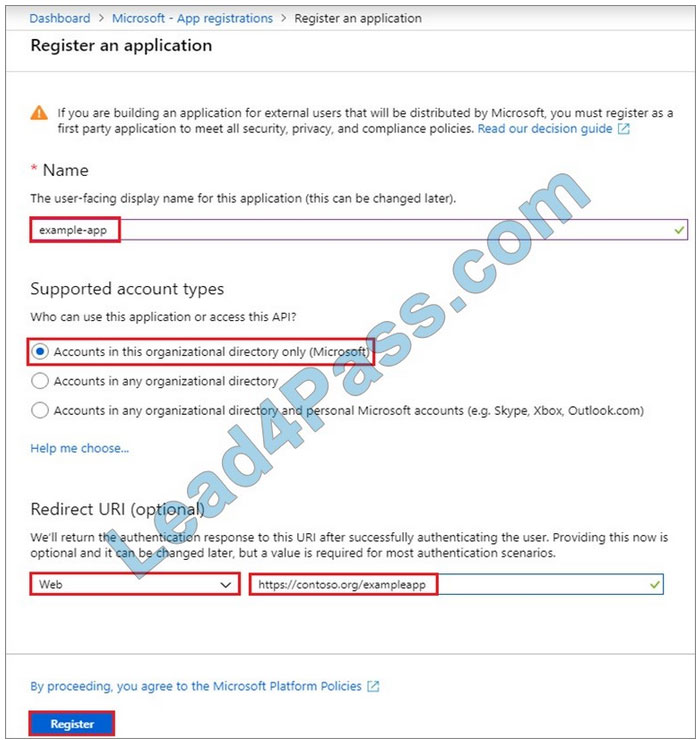
5.
Name the application App10598168. Select a supported account type, which determines who can use the application. Under Redirect URI, select Web for the type of application you want to create. Enter the URI: https://www.contoso.com, where the access token is sent to.
6.
Click Register
Step 2: Create a new application secret
If you choose not to use a certificate, you can create a new application secret.
7 Select Certificates and secrets.
8.
Select Client secrets -> New client secret.
9.
Provide a description of the secret and a duration. When done, select Add.
After saving the client’s secret, the value of the client’s secret is displayed. Copy this value because you aren\’t able to retrieve the key later. You provide the key value with the application ID to sign in as the application. Store the key-value where your application can retrieve it.
Question 7:
SIMULATION
You need to create a new Azure Active Directory (Azure AD) directory named 11641655.onmicrosoft.com and a user named User1 in the new directory. The solution must ensure that User1 is enabled for Azure Multi-Factor Authentication (MFA).
To complete this task, sign in to the Azure portal.
A. See the below.
Correct Answer: A
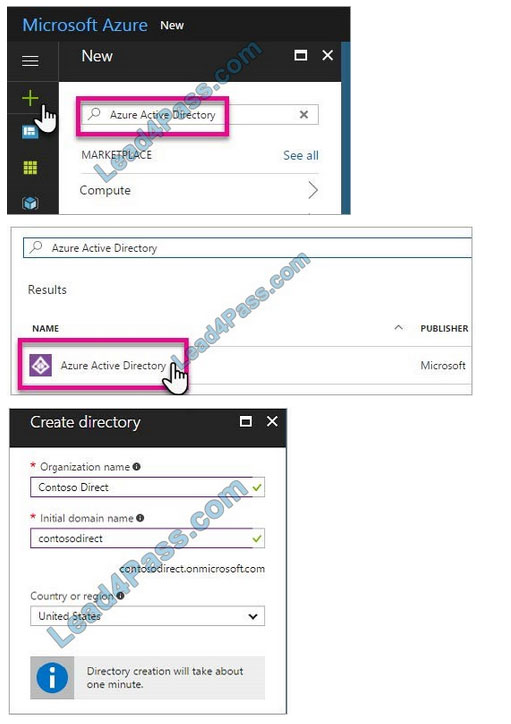
Step 1: Create an Azure Active Directory tenant
1.
Browse to the Azure portal and sign in with an account that has an Azure subscription.
2.
Select the plus icon (+) and search for Azure Active Directory.
3.
Select Azure Active Directory in the search results.
4.
Select Create.
5.
Provide an Organization name and an Initial domain name (10598168). Then select Create. Your directory is created.
6.
After directory creation is complete, select the information box to manage your new directory. Next, you\’re going to add tenant users.
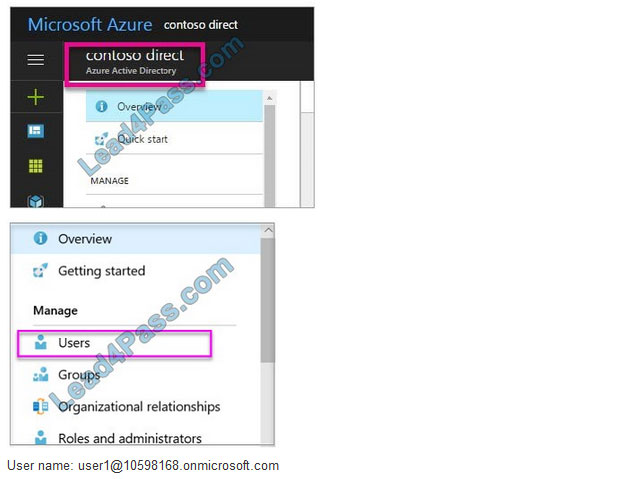
Step 2: Create an Azure Active Directory tenant user
7.
In the Azure portal, make sure you are on the Azure Active Directory fly out.
8.
Under Manage, select Users.
9.
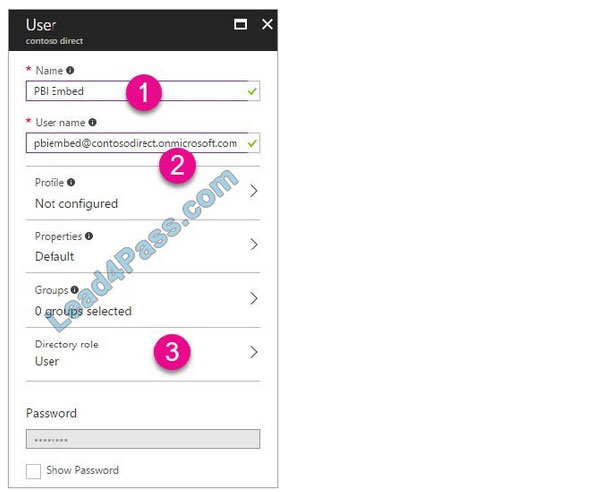
Select All users and then select + New user.
10.
Provide a Name and User name (user1) for the regular user tenant You can also show the temporary password. When you\’re done, select Create. Name: user1
Reference: https://docs.microsoft.com/en-us/power-bi/developer/create-an-azure-active-directory-tenant
Question 8:
SIMULATION
You need to configure Azure to allow RDP connections from the Internet to a virtual machine named VM1. The solution must minimize the attack surface of VM1.
To complete this task, sign in to the Azure portal.
A. See the below.
Correct Answer: A
Explanation:
To enable the RDP port in an NSG, follow these steps:
1.
Sign in to the Azure portal.
2.
In Virtual Machines, select VM1
3.
In Settings, select Networking.
4.
In Inbound port rules, check whether the port for RDP is set correctly. The following is an example of the configuration:
Priority: 300 Name: Port_3389 Port(Destination): 3389 Protocol: TCP Source: Any Destinations: Any Action: Allow
Reference: https://docs.microsoft.com/en-us/azure/virtual-machines/troubleshooting/troubleshoot-rdp-nsg-problem
Question 9:
SIMULATION
You need to add the network interface of a virtual machine named VM1 to an application security group named ASG1.
To complete this task, sign in to the Azure portal.
A. See the below.
Correct Answer: A
1.
In the Search resources, services, and docs box at the top of the portal, begin typing the name of a virtual machine, VM1 that has a network interface that you want to add to, or remove from, an application security group.
2.
When the name of your VM appears in the search results, select it.
3.
Under SETTINGS, select Networking. Select Configure the application security groups, select the application security groups that you want to add the network interface to, or unselect the application security groups that you want to remove the network interface from, and then select Save.
Reference: https://docs.microsoft.com/en-us/azure/virtual-network/virtual-network-network-interface
Question 10:
SIMULATION
You need to perform a full malware scan every Sunday at 02:00 on a virtual machine named VM1 by using Microsoft Antimalware for Virtual Machines.
To complete this task, sign in to the Azure portal.
A. See the below.
Correct Answer: A
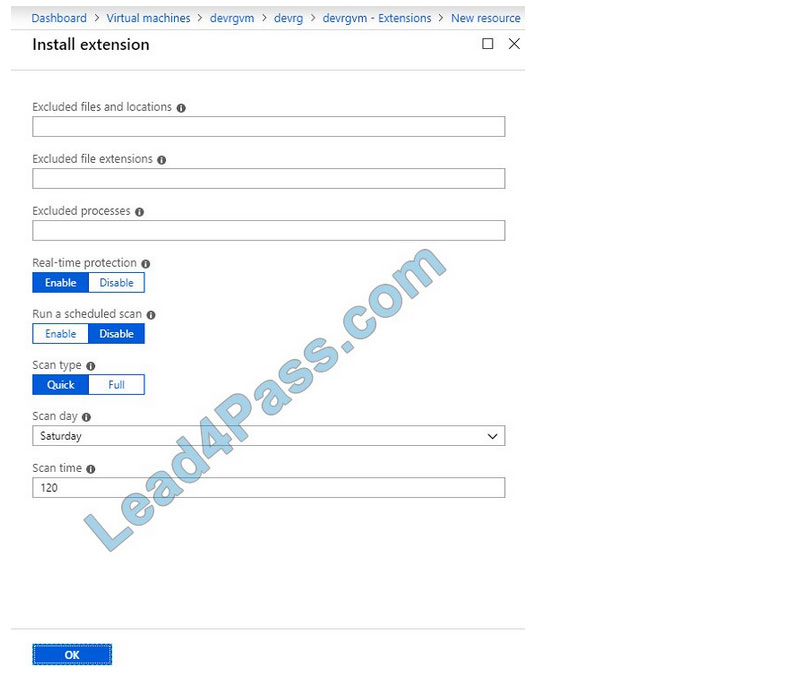
Deploy the Microsoft Antimalware Extension using the Azure Portal for single VM deployment
1.
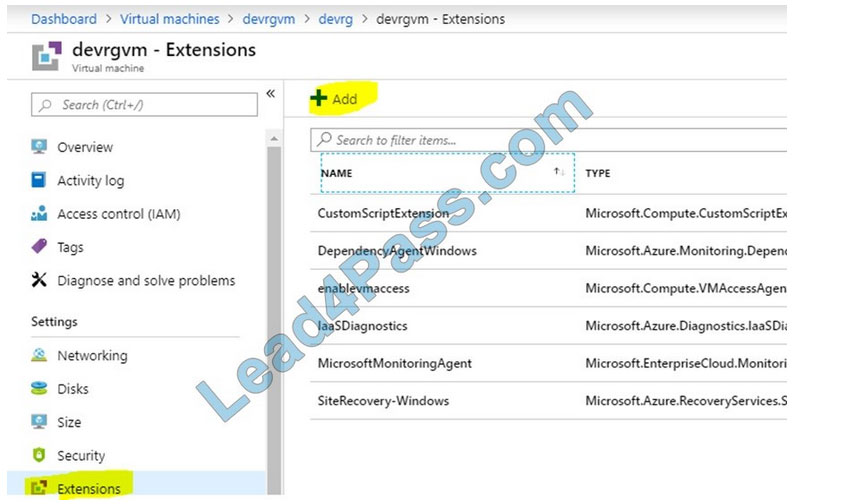
In Azure Portal, go to the Azure VM1\’s blade, navigate to the Extensions section, and press Add.
2.
Select the Microsoft Antimalware extension and press Create.
3.
Fill out the “Install extension” form as desired and press OK. Scheduled: Enable Scan type: Full Scan day: Sunday

Reference: https://www.e-apostolidis.gr/microsoft/azure/azure-vm-antimalware-extension-management/
Question 11:
SIMULATION
You need to prevent administrative users from accidentally deleting a virtual network named VNET1. The administrative users must be allowed to modify the settings of VNET1.
To complete this task, sign in to the Azure portal.
A. See the below.
Correct Answer: A
Explanation:
Locking prevents other users in your organization from accidentally deleting or modifying critical resources, such as Azure subscription, resource group, or resource.
Note: In Azure, the term resource refers to an entity managed by Azure. For example, virtual machines, virtual networks, and storage accounts are all referred to as Azure resources.
1. In the Settings blade for virtual network VNET, select Locks.
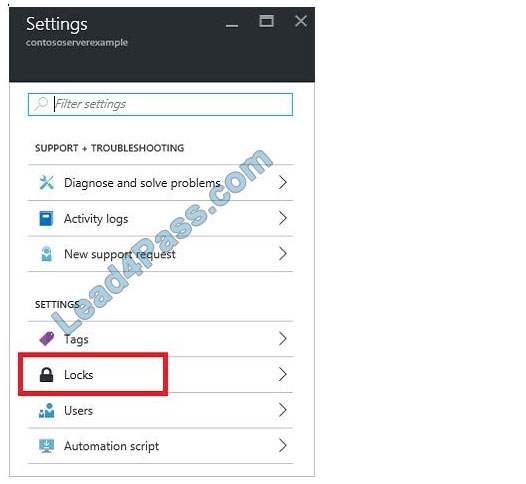
2. To add a lock, select Add.
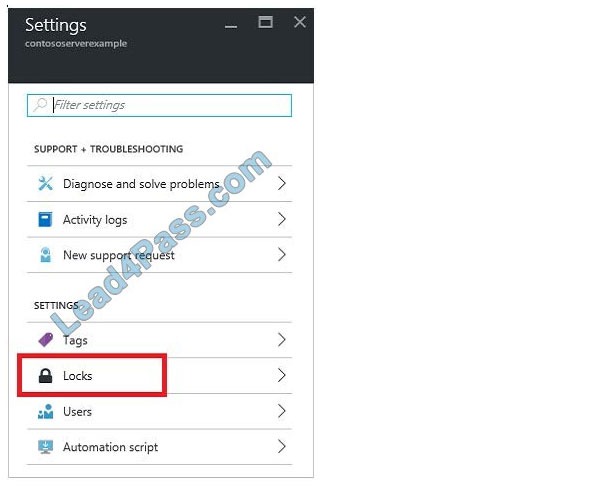
3. For Lock type select Delete lock, and click OK
Reference: https://docs.microsoft.com/en-us/azure/azure-resource-manager/resource-group-lock-resources
Question 12:
SIMULATION
You need to ensure that only devices connected to a 131.107.0.0/16 subnet can access data in the rg1lod10598168 Azure Storage account.
To complete this task, sign in to the Azure portal.
A. See the below.
Correct Answer: A
Step 1:
1.
In the Azure portal go to the storage account you want to secure. Here: rg1lod10598168
2.
Click on the settings menu called Firewalls and virtual networks.
3.
To deny access by default, choose to allow access from Selected networks. To allow traffic from all networks, choose to allow access from All networks.
4.
Click Save to apply your changes.
Step 2:
1.
Go to the storage account you want to secure. Here: rg1lod10598168
2.
Click on the settings menu called Firewalls and virtual networks.
3.
Check that you\’ve selected to allow access from Selected networks.
4.
To grant access to a virtual network with a new network rule, under Virtual networks, click Add an existing virtual network, select Virtual networks, and Subnets options. Enter the 131.107.0.0/16 subnet and then click Add.
Note: When network rules are configured, only applications requesting data over the specified set of networks can access a storage account. You can limit access to your storage account to requests originating from specified IP addresses, IP ranges, or from a list of subnets in an Azure Virtual Network (VNet).
Reference: https://docs.microsoft.com/en-us/azure/storage/common/storage-network-security
Question 13:
SIMULATION
You need to email an alert to a user named [email protected] if the average CPU usage of a virtual machine named VM1 is greater than 70 percent for a period of 15 minutes.
To complete this task, sign in to the Azure portal.
A. See the below.
Correct Answer: A
Create an alert rule on a metric with the Azure portal
1.
In the portal, locate the resource, here VM1, you are interested in monitoring, and select it.
2.
Select Alerts (Classic) under the MONITORING section. The text and icon may vary slightly for different resources.
3.
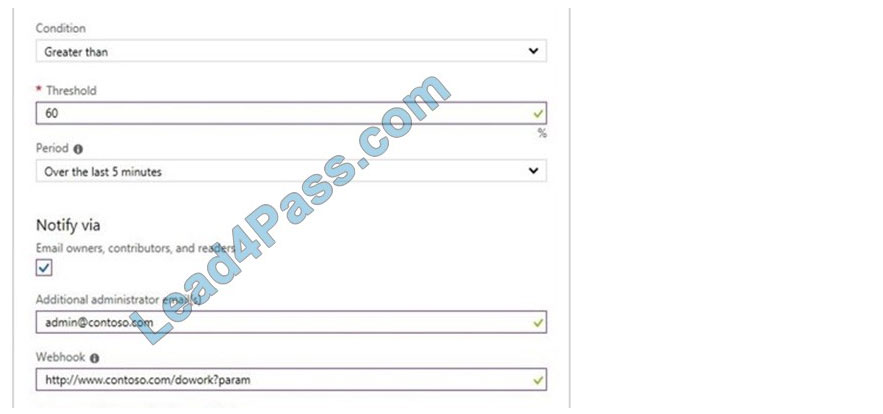
Select the Add metric alert (classic) button and fill in the fields as per below, and click OK.
Metric: CPU Percentage Condition: Greater than Period: Over last 15 minutes Notify via email Additional administrator email(s): [email protected]
Reference: https://docs.microsoft.com/en-us/azure/sql-database/sql-database-insights-alerts-portal
Question 14:
SIMULATION
You need to collect all the audit failure data from the security log of a virtual machine named VM1 to an Azure Storage account.
To complete this task, sign in to the Azure portal.
This task might take several minutes to complete You can perform other tasks while the task completes.
A. See the below.
Correct Answer: A
Step 1: Create a workspace
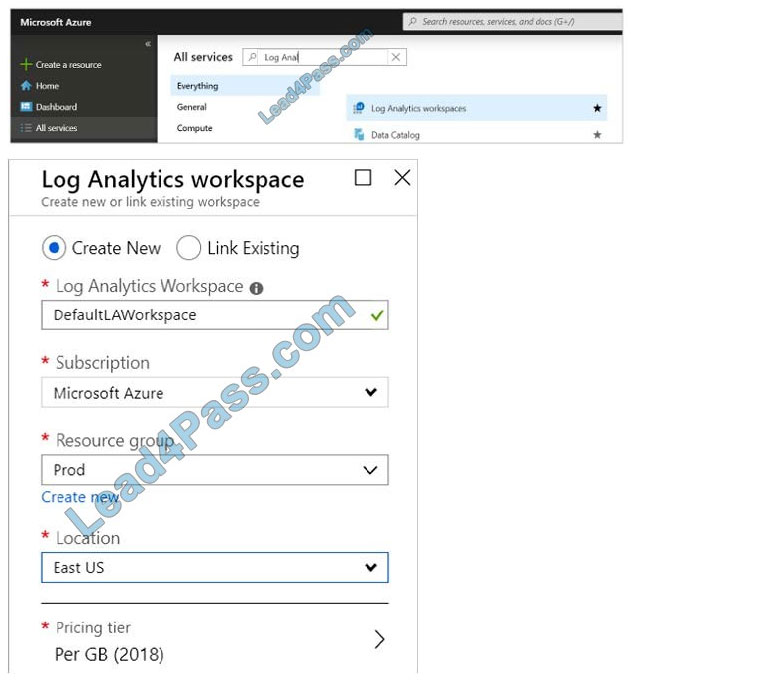
Azure Monitor can collect data directly from your Azure virtual machines into a Log Analytics workspace for detailed analysis and correlation.
1.
In the Azure portal, select All services. In the list of resources, type Log Analytics. As you begin typing, the list filters based on your input. Select Log Analytics workspaces.
2.
Select Create, and then select choices for the following items:
3.
After providing the required information on the Log Analytics workspace pane, select OK.
While the information is verified and the workspace is created, you can track its progress under Notifications from the menu.
Step 2: Enable the Log Analytics VM Extension
Installing the Log Analytics VM extension for Windows and Linux allows Azure Monitor to collect data from your Azure VMs.
1.
In the Azure portal, select All services found in the upper left-hand corner. In the list of resources, type Log Analytics. As you begin typing, the list filters based on your input. Select Log Analytics workspaces.
2.
In your list of Log Analytics workspaces, select DefaultWorkspace (the name you created in step 1).
3.
On the left-hand menu, under Workspace Data Sources, select Virtual machines.
4.
In the list of Virtual machines, select a virtual machine you want to install the agent on. Notice that the Log Analytics connection status for the VM indicates that it is not connected.
5.
In the details for your virtual machine, select Connect. The agent is automatically installed and configured for your Log Analytics workspace. This process takes a few minutes, during which time the Status shows Connecting.
After you install and connect the agent, the Log Analytics connection status will be updated with This workspace.
Reference: https://docs.microsoft.com/en-us/azure/azure-monitor/learn/quick-collect-azurevm
Question 15:
SIMULATION
You need to prevent HTTP connections to the rg1lod10598168n1 Azure Storage account.
To complete this task, sign in to the Azure portal.
A. See the below.
Correct Answer: A
The “Secure transfer required” feature is now supported in Azure Storage account. This feature enhances the security of your storage account by enforcing all requests to your account through a secure connection. This feature is disabled by default.
1.
In Azure Portal select your Azure Storage account rg1lod10598168n1.
2.
Select Configuration, and Secure Transfer required.
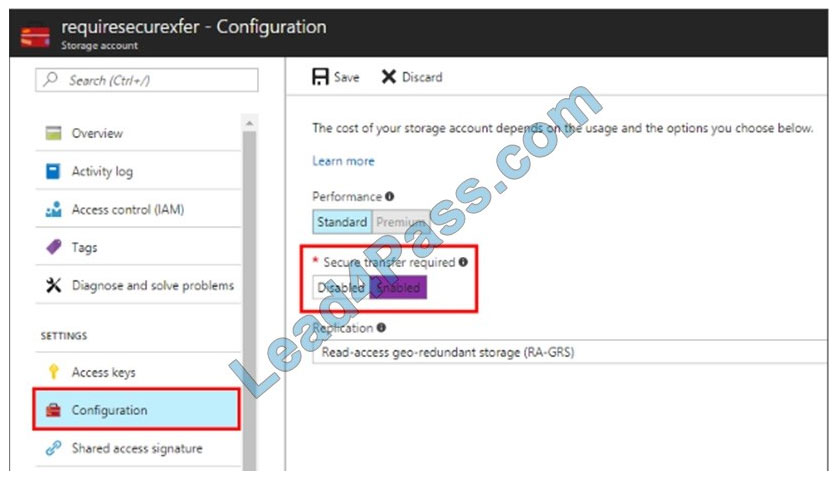
……
Why Choose leads4pass AZ-500 Dumps?
First of all, leads4pass AZ-500 dumps provides the most accurate exam questions and answers, which is a reputation accumulated over the years
Secondly, leads4pass provides two learning methods, PDF and VCE, which makes learning easier, and our model helps more candidates with financial difficulties to have more choices and more favorable prices
Finally, the leads4pass AZ-500 dumps material is really valid exam questions and answers designed around the core of the Microsoft Azure Security Technologies exam.
Well, the right choice will help you successfully pass the exam on the first try and save even more, download the AZ-500 dumps now:https://www.leads4pass.com/az-500.html,
Make the Microsoft Azure Security Technologies exam easier.
You may also like
Recent Posts
Categories
Microsoft Exam Dumps PDF Download
Microsoft Azure Exam PDF Free Download
- Microsoft az-104 PDF Free Download
- Microsoft az-120 PDF Free Download
- Microsoft az-140 PDF Free Download
- Microsoft az-204 PDF Free Download
- Microsoft az-220 PDF Free Download
- Microsoft az-305 PDF Free Download
- Microsoft az-400 PDF Free Download
- Microsoft az-500 PDF Free Download
- Microsoft az-700 PDF Free Download
- Microsoft az-800 PDF Free Download
- Microsoft az-801 PDF Free Download
Microsoft Data Exam PDF Free Download
- Microsoft AI-102 PDF Free Download
- Microsoft DP-100 PDF Free Download
- Microsoft DP-203 PDF Free Download
- Microsoft DP-300 PDF Free Download
- Microsoft DP-420 PDF Free Download
- Microsoft DP-600 PDF Free Download
Microsoft Dynamics 365 Exam PDF Free Download
- Microsoft MB-230 PDF Free Download
- Microsoft MB-240 PDF Free Download
- Microsoft MB-310 PDF Free Download
- Microsoft MB-330 PDF Free Download
- Microsoft MB-335 PDF Free Download
- Microsoft MB-500 PDF Free Download
- Microsoft MB-700 PDF Free Download
- Microsoft MB-800 PDF Free Download
- Microsoft MB-820 PDF Free Download
- Microsoft pl-100 PDF Free Download
- Microsoft pl-200 PDF Free Download
- Microsoft pl-300 PDF Free Download
- Microsoft pl-400 PDF Free Download
- Microsoft pl-500 PDF Free Download
- Microsoft pl-600 PDF Free Download
Microsoft 365 Exam PDF Free Download
- Microsoft MD-102 PDF Free Download
- Microsoft MS-102 PDF Free Download
- Microsoft MS-203 PDF Free Download
- Microsoft MS-700 PDF Free Download
- Microsoft MS-721 PDF Free Download
Microsoft Fundamentals Exam PDF Free Download
- Microsoft 62-193 PDF Free Download
- Microsoft az-900 PDF Free Download
- Microsoft ai-900 PDF Free Download
- Microsoft DP-900 PDF Free Download
- Microsoft MB-910 PDF Free Download
- Microsoft MB-920 PDF Free Download
- Microsoft pl-900 PDF Free Download
- Microsoft MS-900 PDF Free Download
Microsoft Certified Exam PDF Free Download
Recent Comments