Leads4Pass MS-102 practice questions (https://www.leads4pass.com/ms-102.html) are the latest and practical practice questions to guide you in learning effective exam knowledge! In this article, you will get detailed explanations of MS-102 exam questions and answers to help you understand the MS-102 exam topics. Practice free MS-102 exam questions to help you get closer to your goals.
According to MS-102 official news, the latest measurement skills so far are as follows:
MS-102 is a perfect fit for “Administrators who deploy and manage Microsoft 365 and perform tenant-level implementation and management of Microsoft 365 for cloud and hybrid environments”
| Target conditions | Work requirements |
| Functional experience with Microsoft 365 workloads and Microsoft Entra ID (at least one) | Function as the integrating hub for all Microsoft 365 workloads. |
| Networking | Coordinate across multiple Microsoft 365 workloads. |
| Server administration | Work with architects and other administrators responsible for workloads, infrastructure, identity, security, compliance, endpoints, and applications. |
| DNS | |
| PowerShell |
Remember, practice is crucial to mastering any skill, and preparing for the MS-102 exam is no exception. So, grab this opportunity to challenge yourself and deepen your understanding of Microsoft 365 Administrator knowledge.
Practice MS-102 free Q&A to start learning!
Latest updated MS-102 exam questions:
Table of contents:
- Microsoft 365 admins on role-based access control (RBAC) configuration management
- Configuration and management of data protection for Microsoft 365 administrators
- Microsoft 365 Administrator on user identity management and Azure Active Directory sync configuration
- Configuration of Microsoft 365 administrators’ in-service health monitoring and rights management
- Microsoft 365 administrator configuration for eDiscovery and content management
- Configuration of security policies and group management by Microsoft 365 administrators
- Security management and compliance role configuration for Microsoft 365
- Information protection and sensitivity label management for Microsoft 365
- Device management and security configuration for Microsoft 365, specifically implementing Attack Surface Reduction (ASR) rules
- Device grouping and tag management for Microsoft Defender for Endpoint in Microsoft 365
- Email security and policy configuration for Microsoft 365
- Email security and anti-malware policy management for Microsoft 365
- Role-based access control (RBAC) and security management in Microsoft 365
- Compliance management and security configuration for Microsoft 365
- Frequently Asked Questions
- Summary
Core Overview: Microsoft 365 admins on role-based access control (RBAC) configuration management
Q1: You have a Microsoft 365 E5 subscription that contains the users shown in the following table.
You are implementing Microsoft Defender for Endpoint
You must enable role-based access control (RBAQ to restrict access to the Microsoft 365 Defender portal.
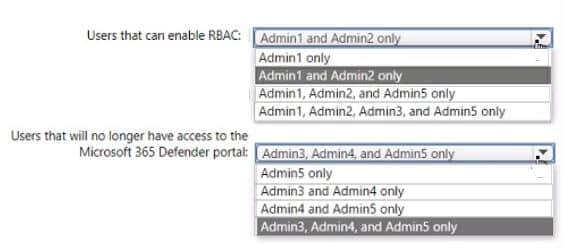
Which users can enable RBAC, and winch users will no longer have access to the Microsoft 365 Defender portal after RBAC is enabled? To answer, select the appropriate options in the answer area.
NOTE Each correct selection is worth one point.
Hot Area:
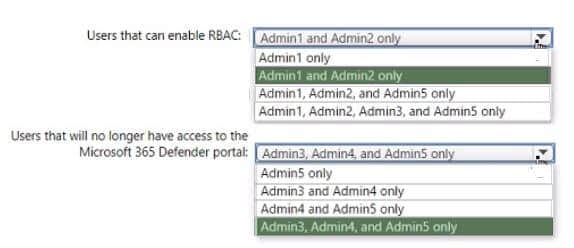
Correct Answer:
Core Overview: Configuration and management of data protection for Microsoft 365 administrators
Q2: You have a Microsoft 365 E5 tenant.
You have a sensitivity label configured as shown in the Sensitivity label exhibit. (Click the Sensitivity label tab.)
You have an auto-labeling policy as shown in the Auto-labeling policy exhibit. (Click the Auto-labeling policy tab.)
A user sends an email that contains the components shown in the following table.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
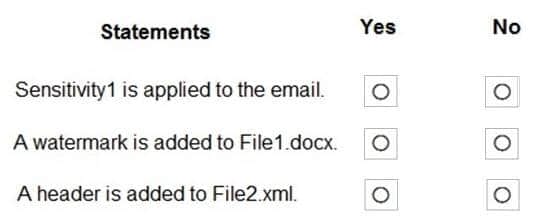
Correct Answer:
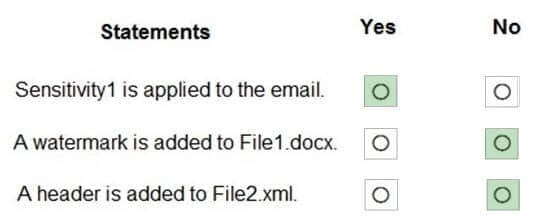
Core Overview: Microsoft 365 Administrator on user identity management and Azure Active Directory sync configuration
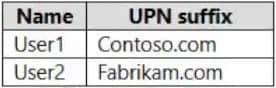
Q3: Your network contains an on-premises Active Directory domain named contoso.com. The domain contains the users shown in the following table.
The domain syncs to an Azure AD tenant named contoso.com as shown in the exhibit. (Click the Exhibit tab.)
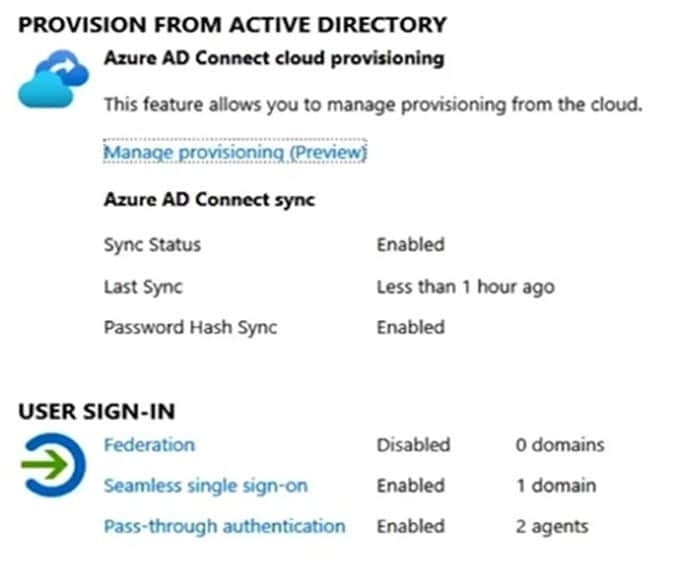
User2 fails to authenticate to Azure AD when signing in as [email protected].
You need to ensure that User2 can access the resources in Azure AD.
Solution: From the on-premises Active Directory domain, you set the UPN suffix for User2 to @contoso.com. You instruct User2 to sign in as [email protected].
Does this meet the goal?
A. Yes
B. No
Correct Answer: A
Explanation:
The on-premises Active Directory domain is named contoso.com. You can enable users to sign on using a different UPN (different domain), by adding the domain to Microsoft 365 as a custom domain. Alternatively, you can configure the user account to use the existing domain (contoso.com).
Core Overview: Configuration of Microsoft 365 administrators in-service health monitoring and rights management
Q4: You have a Microsoft 365 subscription.
You view the Service health Overview as shown in the following exhibit.
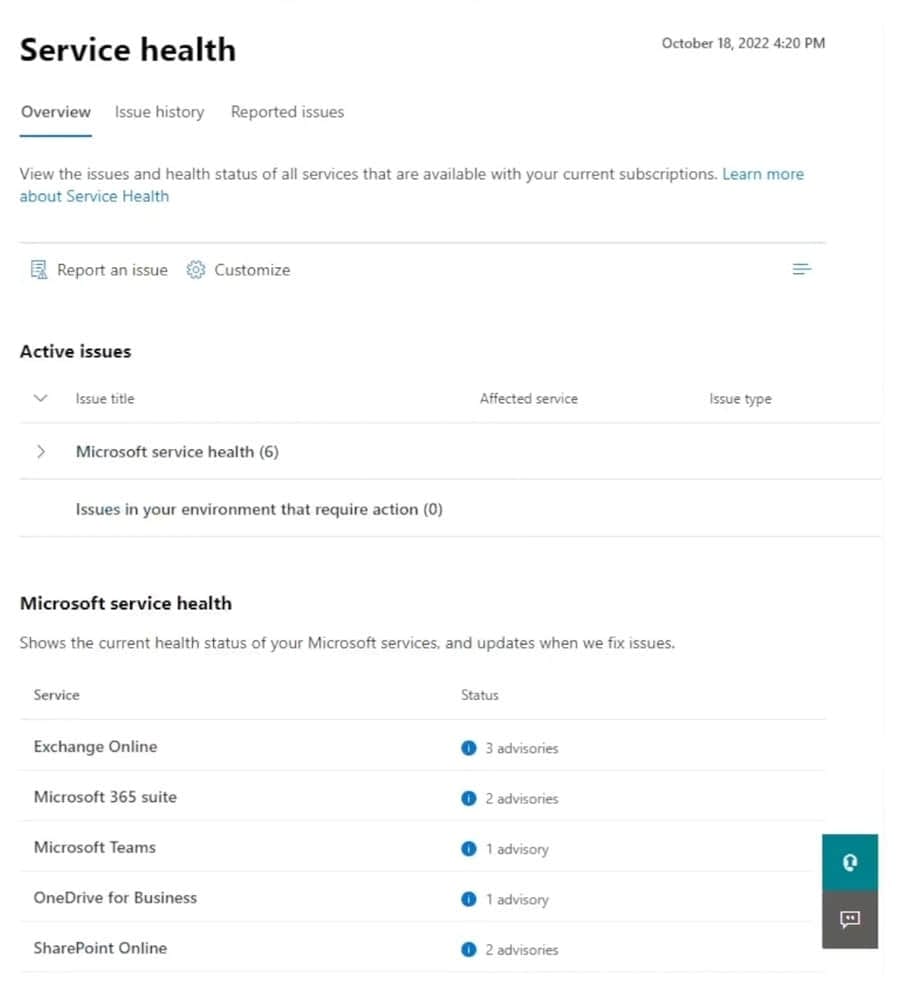
You need to ensure that a user named User1 can view the advisories to investigate service health issues.
Which role should you assign to User1?
A. Message Center Reader
B. Reports Reader
C. Service Support Administrator
D. Compliance Administrator
Correct Answer: C
Explanation:
Service Support admin
Assign the Service Support admin role as an additional role to admins or users who need to do the following in addition to their usual admin role:
-Open and manage service requests
-View and share Message center posts
-Monitor service health
Incorrect:
* Message center reader
Assign the Message center reader role to users who need to do the following:
-Monitor message center notifications
-Get weekly email digests of message center posts and updates
-Share Message center posts
-Have read-only access to Azure AD services, such as users and groups
* Reports reader
Assign the Reports reader role to users who need to do the following:
-View usage data and activity reports in the Microsoft 365 admin center
–
Get access to the Power BI adoption content pack
–
Get access to sign-in reports and activity in Azure AD
-View data returned by Microsoft Graph reporting API
Reference:
Core Overview: Microsoft 365 administrator configuration for eDiscovery and content management
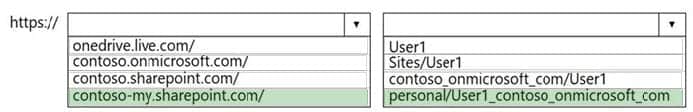
Q5: You have a Microsoft 365 subscription that links to an Azure Active Directory (Azure AD) tenant named contoso.onmicrosoft.com.
A user named User1 stores documents in Microsoft OneDrive.
You need to place the contents of User1\’s OneDrive account on an eDiscovery hold.
Which URL should you use for the eDiscovery hold? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:

Correct Answer:
Core Overview: Configuration of security policies and group management by Microsoft 365 administrators
Q6: You have a Microsoft 365 tenant that contains the groups shown in the following table.
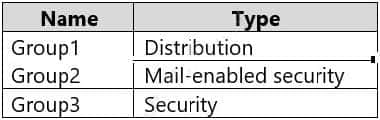
You plan to create a new Windows 10 Security Baseline profile. To which groups can you assign to the profile?
A. Group3 only
B. Group1 and Group3 only
C. Group2 and Group3 only
D. Group1. Group2. and Group3
Correct Answer: A
Explanation:
In Microsoft 365, Windows 10 Security Baseline profiles can typically only be assigned to security groups. Distribution groups (Group1) and mail-enabled security groups (Group2) are mainly used for email distribution and permission control, not for direct security policy enforcement. Therefore, only pure security groups (Group 3) can be assigned Windows 10 security baseline profiles to ensure that relevant security settings and policies can be correctly applied to members of this group.
Reference: https://docs.microsoft.com/en-us/mem/intune/protect/security-baselines-configure#create- the-profile https://docs.microsoft.com/en-us/microsoft-365/admin/create-groups/compare- groups?view=o365-worldwide
Core Overview: Security management and compliance role configuration for Microsoft 365
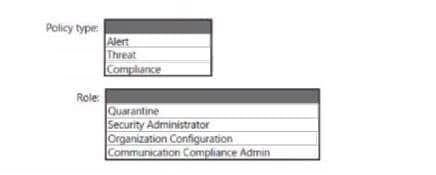
Q7: You have a Microsoft 365 E5 tenant.
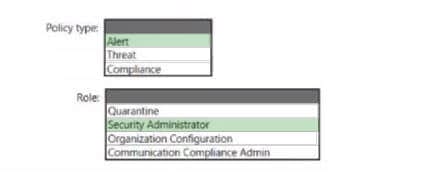
You need to ensure that administrators are notified when a user receives an email message that contains malware. The solution must use the principle of least privilege.
Which type of policy should you create and which Microsoft 365 compliance center role is required to create the pokey? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
Correct Answer:
Core Overview: Information protection and sensitivity label management for Microsoft 365
Q8: You have a Microsoft 365 E5 tenant.
You configure sensitivity labels.
Users report that the Sensitivity button is unavailability in Microsoft Word for the web. The sensitivity button is available in Word for Microsoft 365.
You need to ensure that the users can apply the sensitivity labels when they use Word for the web.
What should you do?
A. Copy policies from Azure Information Protection to the Microsoft 365 Compliance Center
B. Publish the sensitivity labels.
C. Create an auto-labeling policy
D. Enable sensitivity labels for files in Microsoft SharePoint Online and OneDrive.
Correct Answer: B
Explanation:
When users report that the “Sensitivity” button is unavailable in Word for the web, it typically indicates that the sensitivity labels have not been published to the users. Sensitivity labels must be explicitly published within the Microsoft 365 compliance center so that they become visible and usable within supported applications.
- Publish Sensitivity Labels: In the Microsoft 365 compliance center, administrators need to create or configure sensitivity labels and publish them to specific users or groups of users. The publishing action ensures that these labels are visible in the users’ Office applications and can be used to tag and protect documents.
- Check User Groups: Ensure that the published labels include the user groups who reported the issue.
- Confirm Application Support: While the Word for Microsoft 365 client might support certain features, support in the web version of Word might differ slightly. Verify that the published labels are supported in the web application as well.
By following these steps, you can ensure that users are able to access and apply sensitivity labels while using Word for the web, thereby maintaining the security and compliance of their documents.
Core Overview: Device management and security configuration for Microsoft 365, specifically implementing Attack Surface Reduction (ASR) rules
Q9: You have a Microsoft 365 E5 tenant that contains the devices shown in the following table.
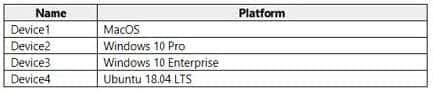
You plan to implement attack surface reduction (ASR) rules. Which devices will support the ASR rules?
A. Device 1, Device2, and Device3 only
B. Device3 only
C. Device2 and Device3 only
D. Device1, Device2, Devices and Device4
Correct Answer: C
Explanation:
Device2 (Windows 10 Pro) and Device3 (Windows 10 Enterprise) are both devices running Windows 10. Microsoft’s Attack Surface Reduction (ASR) rules are designed specifically for Windows 10 to help prevent various malware attacks and improve system security.
Device1 (macOS) and Device4 (Ubuntu 18.04 LTS) are devices running macOS and Ubuntu respectively. These operating systems do not support the ASR rules of Windows 10.
Therefore, only devices running Windows 10 (Device2 and Device3) can support and enforce ASR rules.
Reference:
Core Overview: Device grouping and tag management for Microsoft Defender for Endpoint in Microsoft 365
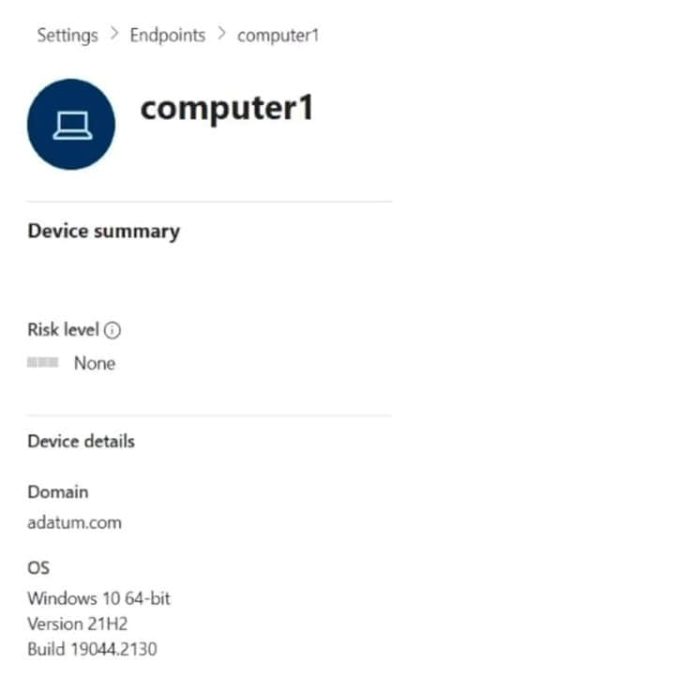
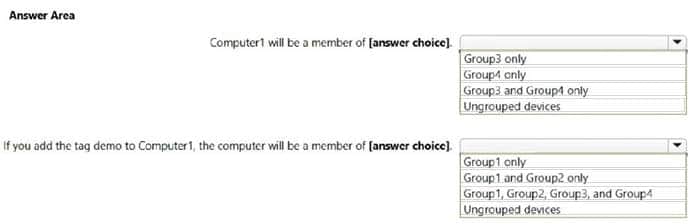
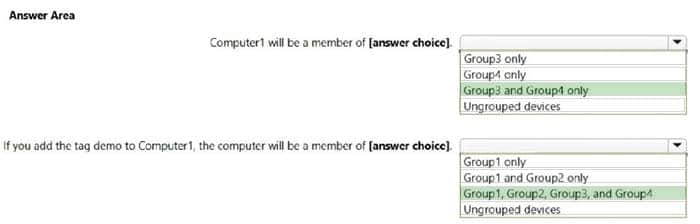
Q10: Your company uses Microsoft Defender for Endpoint. Microsoft Defender for Endpoint includes the device groups shown in the following table.
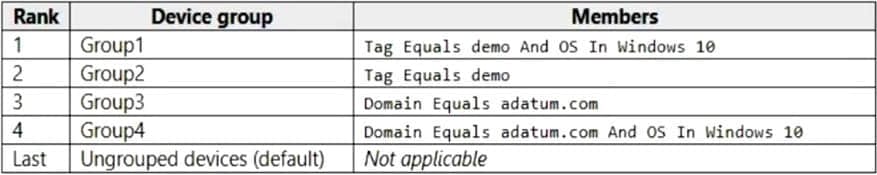
You onboard a computer named computer1 to Microsoft Defender for Endpoint as shown in the following exhibit.
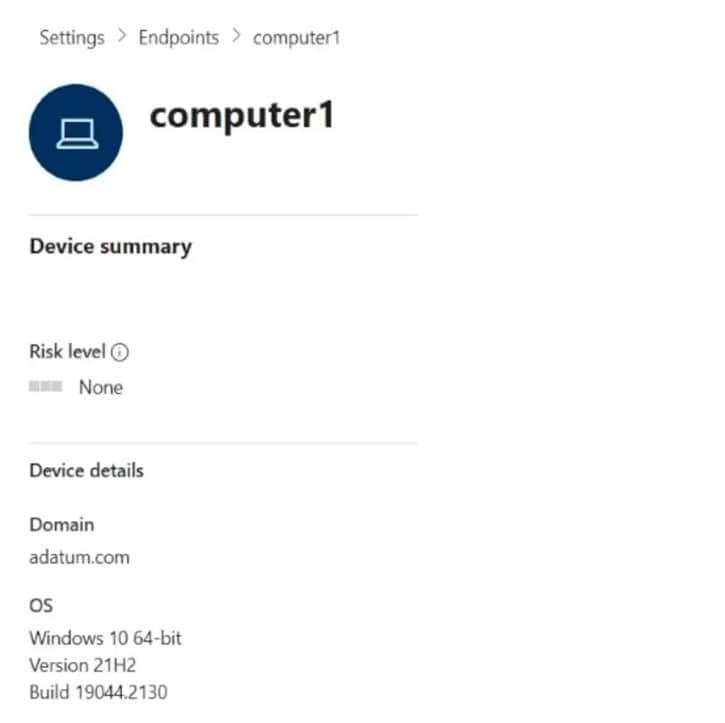
Use the drop-down menus to select the answer choice that completes each statement. NOTE: Each correct selection is worth one point.
Hot Area:
Correct Answer:
Core Overview: Email security and policy configuration for Microsoft 365
Q11: You have a Microsoft 365 subscription that uses Microsoft Defender for Office 365.
You need to configure policies to meet the following requirements:
Customize the common attachments filter.
Enable impersonation protection for sender domains.
Which type of policy should you configure for each requirement? To answer, drag the appropriate policy types to the correct requirements. Each policy type may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
Select and Place:

Correct Answer:

Core Overview: Email security and anti-malware policy management for Microsoft 365
Q12: You have a Microsoft 365 E5 subscription that contains a user named User1.
The subscription has a single anti-malware policy as shown in the following exhibit.
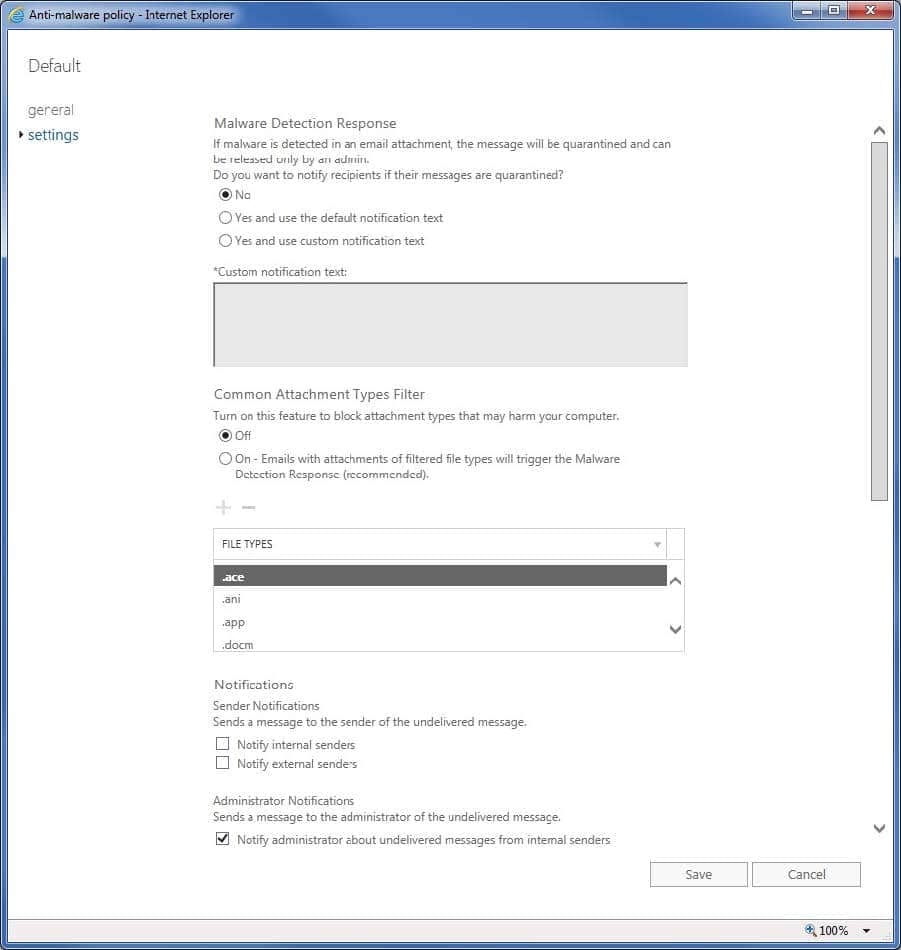
An email message that contains text and two attachments is sent to User1. One attachment is infected with malware. How will the email message and the attachments be processed?
A. Both attachments will be removed. The email message will be quarantined, and Used will receive an email message without any attachments and an email message that includes the following text: \’Malware was removed.\’
B. The email message will be quarantined, and the message will remain undelivered.
C. Both attachments will be removed. The email message will be quarantined, and User1 will receive a copy of the message containing the original text and a new attachment that includes the following text: \’Malware was removed.”
D. The malware-infected attachment will be removed. The email message will be quarantined, and User1 will receive a copy of the message containing only the uninfected attachment.
Correct Answer: C
Explanation:
Based on the displayed anti-malware policy settings, when malware is detected, attachments containing malware will be removed and the entire message will be quarantined. According to the description of the policy, after the attachment in the email is removed, the user will receive an email containing the original text and an attached text file stating “The malware has been removed”, which is consistent with the description of option C. processing method.
Reference:
Core Overview: Role-based access control (RBAC) and security management in Microsoft 365
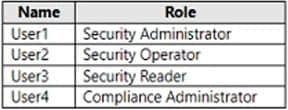
Q13: You have an Azure AD tenant and a Microsoft 365 E5 subscription. The tenant contains the users shown in the following table.
You plan to implement Microsoft Defender for Endpoint.
You verify that role-based access control (RBAC) is turned on in Microsoft Defender for Endpoint.
You need to identify which user can view security incidents from the Microsoft 365 Defender portal.
Which user should you identify?
A. User1
B. User2
C. User3
D. User4
Correct Answer: A
Explanation:
As a security administrator, User1 usually has permission to view and manage security events, including viewing security events from Microsoft Defender for Endpoint.
User2 (Security Operator) and User3 (Security Reader) may have permission to view some security-related information, but their permissions are not as broad as Security Administrators.
User4 (Compliance Administrator) is primarily focused on compliance tasks rather than direct security incident management.
Therefore, to view security events in the Microsoft 365 Defender portal, User1 should be selected because he, as the security administrator, has the required permissions and access capabilities.
Core Overview: Compliance management and security configuration for Microsoft 365
Q14: You have a Microsoft 365 tenant that has Enable Security defaults set to No in Azure Active Directory (Azure AD).
The tenant has two Compliance Manager assessments as shown in the following table.
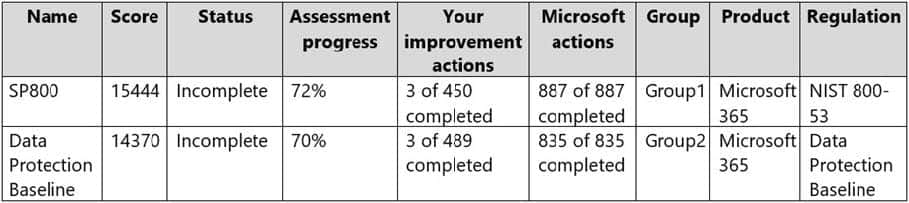
The SP800 assessment has the improvement actions shown in the following table.
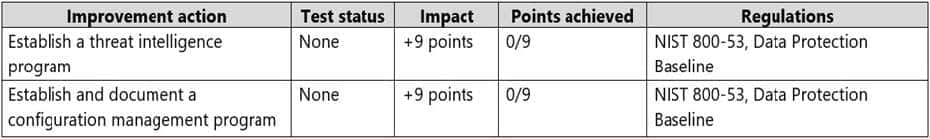
You perform the following actions:
For the Data Protection Baseline assessment, change the Test status of Establish a threat intelligence program to Implemented.
Enable multi-factor authentication (MFA) for all users.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:

Correct Answer:

Frequently Asked Questions
Is Microsoft MS-102 difficult?
Quite difficult! Preparing for the Microsoft MS-102 exam can be very challenging and time-consuming. Many candidates face various obstacles such as a lack of authentic exam questions or high cost associated with Microsoft MS-102 exam dumps.
Is MS-102 Certification Worth It?
Obtaining Microsoft 365 certification through the MS-102 exam: Administrator Expert Certificate can bring you the following advantages: Verification of professional skills: This certificate demonstrates your professional ability in managing and securing Microsoft 365 environments.
How many attempts are allowed on the MS-102 exam?
You can pass the MS-102 exam in five attempts. A 14-day interval is required between each attempt.
What positions can be obtained with MS-102 certification?
- Microsoft 365 AdministratorManages and optimizes Microsoft 365 applications and services to ensure productivity and collaboration within organizations
- Messaging EngineerDesigns and implements advanced messaging solutions, including complex configurations and hybrid environments
- Messaging ArchitectSpecializes in designing comprehensive messaging architectures that align with an organization’s collaboration and communication needs
- Security AnalystFocuses on email security and cybersecurity, protecting email systems from threats and vulnerabilities
- Cloud AdministratorExpands skills to manage cloud-based collaboration and messaging platforms like Google Workspace or Microsoft 365
Summary
We hope you enjoy studying with these latest MS-102 exam questions and answers. At the same time, we recommend that you avoid using any MS-102 exam materials available on the web as they may become outdated very quickly. What’s more, using this information may result in Microsoft revoking your certification
Therefore, it is recommended that you invest more time in studying the relevant objectives of the exam in depth and attempt MS-102 mock exams. These practice exams are designed to closely resemble the real exam and help you better assess your skill level. When you can consistently score 80-85% on your practice exams, it means you’re ready to tackle the real exam.
Leads4Pass offers a wealth of MS-102 exam practice resources, including practice tests and hands-on labs, to help you gain hands-on experience.
If you have any questions or need further assistance in preparing for the MS-102 exam, please feel free to leave us a comment!